I have now spend endless days what should be a simple problem; and gave up, now asking: what is the best way to set up VLANs.
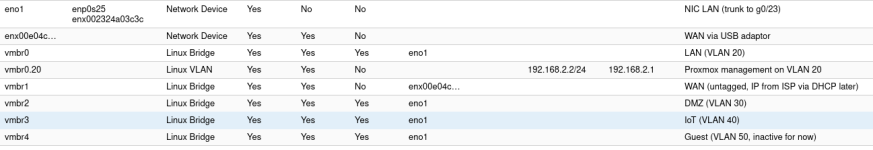
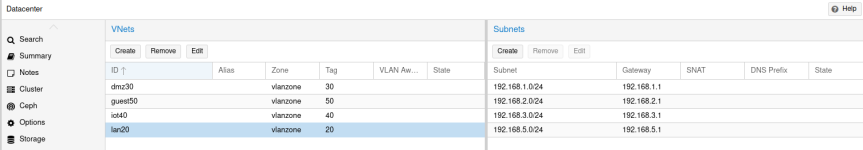
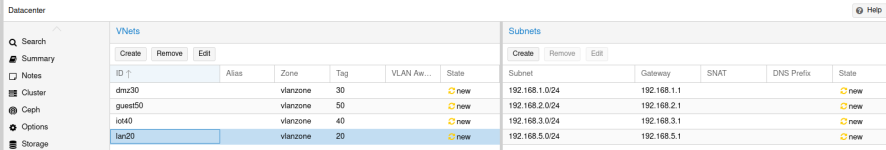
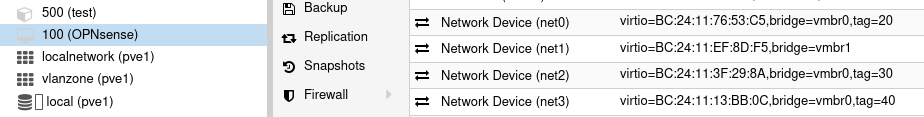
The way I understand it (and I am new to VLANs), is to set a trunk port on the switch (I have set VIDs 20 30 40 50) and access port for VID 20 (=LAN); Proxmox is 192.168.2.2 and has vmbr0 tagged with VIDs 20 30 40 50. This should allow my PC to access the Proxmox GUI. Is this correct?
The minute I connect both Proxmox .2 and my PC .100 to the tagged ports, I can neither ping .2 nor get to the Proxmox GUI. I have a notebook on this VLAN too .164, and can ping it and vice versa.
What on earth am I missing? (I am not using the Proxmox firewall, and th eOPNsense VM is shut down; just to test this basic network.)
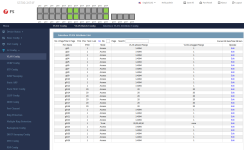
My switch is set up like this:
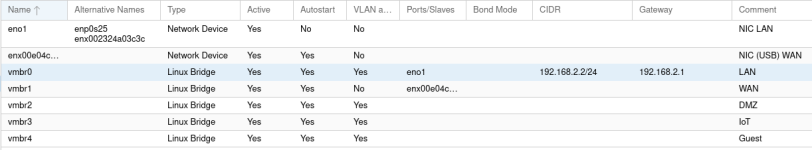
My Proxmox config ie:
or the GUI equivalent...
The way I understand it (and I am new to VLANs), is to set a trunk port on the switch (I have set VIDs 20 30 40 50) and access port for VID 20 (=LAN); Proxmox is 192.168.2.2 and has vmbr0 tagged with VIDs 20 30 40 50. This should allow my PC to access the Proxmox GUI. Is this correct?
The minute I connect both Proxmox .2 and my PC .100 to the tagged ports, I can neither ping .2 nor get to the Proxmox GUI. I have a notebook on this VLAN too .164, and can ping it and vice versa.
What on earth am I missing? (I am not using the Proxmox firewall, and th eOPNsense VM is shut down; just to test this basic network.)
My switch is set up like this:

My Proxmox config ie:
Code:
# [2025-10-01 09:40] root@pve1 ~ #
brctl show
bridge name bridge id STP enabled interfaces
vmbr0 8000.002324a03c3c no eno1
veth103i0
veth104i0
veth105i0
vmbr1 8000.00e04c896ad5 no enx00e04c896ad5
vmbr2 8000.fe13c64dffd6 no veth102i0
vmbr3 8000.000000000000 no
vmbr4 8000.000000000000 no
# [2025-10-01 09:40] root@pve1 ~ #
cat /etc/network/interfaces
# network interface settings; autogenerated
# Please do NOT modify this file directly, unless you know what
# you're doing.
#
# If you want to manage parts of the network configuration manually,
# please utilize the 'source' or 'source-directory' directives to do
# so.
# PVE will preserve these directives, but will NOT read its network
# configuration from sourced files, so do not attempt to move any of
# the PVE managed interfaces into external files!
auto lo
iface lo inet loopback
iface eno1 inet manual
#NIC LAN
auto enx00e04c896ad5
iface enx00e04c896ad5 inet manual
#NIC (USB) WAN
auto vmbr0
iface vmbr0 inet static
address 192.168.2.2/24
gateway 192.168.2.1
bridge-ports eno1
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 20 30 40 50
#LAN
auto vmbr1
iface vmbr1 inet manual
bridge-ports enx00e04c896ad5
bridge-stp off
bridge-fd 0
#WAN
auto vmbr2
iface vmbr2 inet manual
bridge-ports none
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 30
#DMZ
auto vmbr3
iface vmbr3 inet manual
bridge-ports none
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 40
#IoT
auto vmbr4
iface vmbr4 inet manual
bridge-ports none
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 50
#Guest
source /etc/network/interfaces.d/*or the GUI equivalent...

Last edited: