Hi All,
im trying to find out if my server has been hacked or compromised but im confused how it could of happened if it has?
i was doing abit of routine maintance (updates/restarting vms etc)
and i then spotted my SSL certificate for the web port 8006 is including an external IP address i have no idea about?
i have checked the GUI and it has also listed inside the SSL cert?
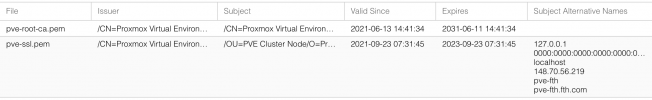
but whats even more frightning is i have part scanned my whole drive for the IP address and its listed in a file for known_hosts too!?
i have checked my interface ip address too incase it was a VPN or something but not listed there either?
my server is located inside my home network with an internal ip address and no DMZ or external access?
the is only a single VM running on the server too as the server isnt powerful (dual core 6gb ram)
any suggestions would be amazing!?
Regards
Simon
im trying to find out if my server has been hacked or compromised but im confused how it could of happened if it has?
i was doing abit of routine maintance (updates/restarting vms etc)
and i then spotted my SSL certificate for the web port 8006 is including an external IP address i have no idea about?

i have checked the GUI and it has also listed inside the SSL cert?

but whats even more frightning is i have part scanned my whole drive for the IP address and its listed in a file for known_hosts too!?
Code:
root@pve-fth:/# grep -rnw * -e '148.70.56.219'
etc/pve/priv/known_hosts:5:148.70.56.219 ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDklgCUPT3D+7frb2U+XQ29drHsJGYgnwRjoG3LEq2diRFtXeULBP0xlSPkhG0g8TeQXWnZTSeASQ1Iw6tTi8Xr5Xfj078FgjMh
qvooSd5k/Q+1xh9QzYGV9dqDBNx2nI/pvDJ+0VFllz/SGMTa6fgS4CzwrwsgFuS6WAt+stUgXiuFsHReJXfyJNDjcIGU63/6aYfXm6EaWlXxBDiFPrAcGN0XUF/vZ1rXUZ0irxM54LD+EXcJmA2Onbqa+YAB8pTupA42YW/Ce//xdrh2+
RDBZzhE/LkRi6i9XR3PUq251wguOoDwCwz03uEugAFKYYNDJ9e+jLyAPN1FppI66UC1i have checked my interface ip address too incase it was a VPN or something but not listed there either?
Code:
root@pve-fth:/# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master vmbr0 state UP group default qlen 1000
link/ether 18:03:73:d7:9c:f7 brd ff:ff:ff:ff:ff:ff
altname enp0s25
3: vmbr0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether 18:03:73:d7:9c:f7 brd ff:ff:ff:ff:ff:ff
inet 192.168.88.88/24 scope global vmbr0
valid_lft forever preferred_lft forever
inet6 fe80::1a03:73ff:fed7:9cf7/64 scope link
valid_lft forever preferred_lft forever
4: tap100i0: <BROADCAST,MULTICAST,PROMISC,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master vmbr0 state UNKNOWN group default qlen 1000
link/ether d2:8e:cd:02:bd:e6 brd ff:ff:ff:ff:ff:ffmy server is located inside my home network with an internal ip address and no DMZ or external access?
the is only a single VM running on the server too as the server isnt powerful (dual core 6gb ram)
any suggestions would be amazing!?
Regards
Simon

