You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
You should be able to integrate this with a Custom Check Script. You can read more about this in our PMG documentation [1].
[1] https://pmg.proxmox.com/pmg-docs/pmg-admin-guide.html#pmgconfig_custom_check
[1] https://pmg.proxmox.com/pmg-docs/pmg-admin-guide.html#pmgconfig_custom_check
Hi. Now i do it with Kaspersky Endpoint Security Linux (KESL)
On this moment i used script like that:
You can test it by sending mail to 'antivirustest@internet-lab.ru' with subject 'I need an Anti-Virus Test File'.
They send you EICAR e-mail, PMG must notify you with mail like:
If you use File_Threat_Protection in KESL, you must add exceptions for 3 directories:
/tmp with * mask for tmp files (files have name like .proxdump_*, exceptions for hiden files don't work, i create ticket for that in Kaspersky support)
/var/spool/pmg/active/ with mask ??????????????????? where mails check
/var/spool/pmg/virus/ with mask ??????????????????? where quarantine mails store
On this moment i used script like that:
Bash:
#! /bin/bash
# you need create manually dir mail_av in /var/log directory by command "mkdir /var/log/mail_av"
# you need install pwgen package for that via command "apt update && apt install pwgen"
# create unical policy name
pol=$(pwgen 10 -1 -s -0)
# create policy file
echo "FirstAction=Skip" > /var/log/mail_av/$pol.pol
echo "ScanMailBases=Yes" >> /var/log/mail_av/$pol.pol
echo "ScanPlainMail=Yes" >> /var/log/mail_av/$pol.pol
echo "UseAnalyzer=Yes" >> /var/log/mail_av/$pol.pol
echo "HeuristicLevel=Medium" >> /var/log/mail_av/$pol.pol
echo "[ScanScope.item_1]" >> /var/log/mail_av/$pol.pol
echo "Path=$2" >> /var/log/mail_av/$pol.pol
# create policy in KESL from file
/opt/kaspersky/kesl/bin/kesl-control --create-task $pol --type ODS --file /var/log/mail_av/$pol.pol >> /dev/null
# check file by KESL
vir=$(/opt/kaspersky/kesl/bin/kesl-control --start-task $pol -W|grep 'DetectName'|awk -F'=' '{print $2}'| head -1)
# remove policy from KESL
/opt/kaspersky/kesl/bin/kesl-control --delete-task $pol
# find virus name in KESL output
if [ -z $vir ]; then
rm -f /var/log/mail_av/$pol.pol
# write result to log that letter good
echo "Mail $2 was checked succesfull" >> /var/log/mail_av/checked
echo "v1"
echo "OK";
else
# write result to log that letter virused
# KESL policy don't delete
echo "In mail $2 find $vir" >> /var/log/mail_av/$pol.pol
echo "Mail $2 was blocked. More info in /var/log/mail_av/$pol.pol file" >> /var/log/mail_av/checked
echo "v1"
echo "VIRUS: $vir"
fi
exit 0You can test it by sending mail to 'antivirustest@internet-lab.ru' with subject 'I need an Anti-Virus Test File'.
They send you EICAR e-mail, PMG must notify you with mail like:
Proxmox Notification:
Sender: antivirustest@internet-lab.ru
Receiver: mailadmin@contoso.com
Targets: mailadmin@contoso.com
Subject: Antivirus test from internet-lab.ru
Matching Rule: Block Viruses
Rule: Block Viruses
Receiver: mailadmin@contoso.com
Action: Move to quarantine.
Action: notify mailadmin@contoso.com
Virus Info: EICAR-Test-File
If you use File_Threat_Protection in KESL, you must add exceptions for 3 directories:
/tmp with * mask for tmp files (files have name like .proxdump_*, exceptions for hiden files don't work, i create ticket for that in Kaspersky support)
/var/spool/pmg/active/ with mask ??????????????????? where mails check
/var/spool/pmg/virus/ with mask ??????????????????? where quarantine mails store
Last edited:
Thank you! Will try.Hi. Now i do it with Kaspersky Endpoint Security Linux (KESL)
On this moment i used script like that:
Bash:#! /bin/bash # you need create manually dir mail_av in /var/log directory by command "mkdir /var/log/mail_av" # you need install pwgen package for that via command "apt update && apt install pwgen" # create unical policy name pol=$(pwgen 10 -1 -s -0) # create policy file echo "FirstAction=Skip" > /var/log/mail_av/$pol.pol echo "ScanMailBases=Yes" >> /var/log/mail_av/$pol.pol echo "ScanPlainMail=Yes" >> /var/log/mail_av/$pol.pol echo "UseAnalyzer=Yes" >> /var/log/mail_av/$pol.pol echo "HeuristicLevel=Medium" >> /var/log/mail_av/$pol.pol echo "[ScanScope.item_1]" >> /var/log/mail_av/$pol.pol echo "Path=$2" >> /var/log/mail_av/$pol.pol # create policy in KESL from file /opt/kaspersky/kesl/bin/kesl-control --create-task $pol --type ODS --file /var/log/mail_av/$pol.pol >> /dev/null # check file by KESL vir=$(/opt/kaspersky/kesl/bin/kesl-control --start-task $pol -W|grep 'DetectName'|awk -F'=' '{print $2}'| head -1) # remove policy from KESL /opt/kaspersky/kesl/bin/kesl-control --delete-task $pol # find virus name in KESL output if [ -z $vir ]; then rm -f /var/log/mail_av/$pol.pol # write result to log that letter good echo "Mail $2 was checked succesfull" >> /var/log/mail_av/checked echo "v1" echo "OK"; else # write result to log that letter virused # KESL policy don't delete echo "In mail $2 find $vir" >> /var/log/mail_av/$pol.pol echo "Mail $2 was blocked. More info in /var/log/mail_av/$pol.pol file" >> /var/log/mail_av/checked echo "v1" echo "VIRUS: $vir" fi exit 0
You can test it by sending mail to 'antivirustest@internet-lab.ru' with subject 'I need an Anti-Virus Test File'.
They send you EICAR e-mail, PMG must notify you with mail like:
If you use File_Threat_Protection in KESL, you must add exceptions for 3 directories:
/tmp with * mask for tmp files (files have name like .proxdump_*, exceptions for hiden files don't work, i create ticket for that in Kaspersky support)
/var/spool/pmg/active/ with mask ??????????????????? where mails check
/var/spool/pmg/virus/ with mask ??????????????????? where quarantine mails store
Is it needed ClamAV to be removed from system?
Last edited:
No.Thank you! Will try.
Is it needed ClamAV to be removed from system?
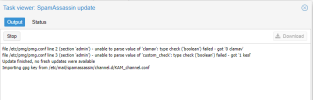
You can disable it via /etc/pmg/pmg.conf
In section admin add 2 lines
section: admin
clamav 0 --disable clamav
custom_check 1 --enable KESL
Thank youNo.
You can disable it via /etc/pmg/pmg.conf
In section admin add 2 lines
section: admin
clamav 0 --disable clamav
custom_check 1 --enable KESL
Finally if I understood correctly (top level steps)
Install kesl on proxmox MG
Create kesl.sh in /usr/local/bin/pmg-custom-check dir (or difine custom path via custom_check_path enviroment)
Correct pmg.conf as you described above
Restart pmg-smtp-filter
Enjoy
Is that correct steps?
/usr/local/bin/pmg-custom-check - not folder, this file with scriptThank you
Finally if I understood correctly (top level steps)
Install kesl on proxmox MG
Create kesl.sh in /usr/local/bin/pmg-custom-check dir (or difine custom path via custom_check_path enviroment)
Correct pmg.conf as you described above
Restart pmg-smtp-filter
Enjoy
Is that correct steps?
And yes, after that steps KESL must start check every e-mail.
If you use KSC and install its agent on host, in KSC you will can see many events
I think you must do same steps, but change KESL commands to symantec specific.Is there any one try to use Symantec? My company use SEP and it has linux agent.
In this manual symantec has key manualscan -s|--scan for starting manual scan.
Try to check manually Eicar msg with this key, see output and find filter for output only virus name.
Thank you very much./usr/local/bin/pmg-custom-check - not folder, this file with script
And yes, after that steps KESL must start check every e-mail.
If you use KSC and install its agent on host, in KSC you will can see many events
Works like a charm.
Last edited:
please post your /etc/pmg/pmg.conf in code-tags - my guess is that you have added `-- disable clamav` there and `--enable kesl`, which is not permitted by the config-parser.... (just remove these parts of the line.I allready follow step but can't using kesl
my version: 8.1.4
for code tags i meant - surround the text you paste (instead of a screenshot in code-tags (click on </> on top of the editor...)I change code tags in /etc/pmg/pmg.conf
for the contents of your config file - it should look like:
Code:
section: admin
clamav 0
custom_check 1Proxmox no longer reports errors, but when attachments are sent, Kaspersky does not scan and block them.for code tags i meant - surround the text you paste (instead of a screenshot in code-tags (click on </> on top of the editor...)
for the contents of your config file - it should look like:
Code:section: admin clamav 0 custom_check 1
anything in the journal from kaspersky? or any other messages? - how does your custom script look like? (keep in mind that the custom script is probably nothing I can help you with too much)
My kesl config in /usr/local/bin/pmg-custom-check
PMG config file /etc/pmg/pmg.conf
The output log when received mail
Code:
#! /bin/bash
# you need create manually dir mail_av in /var/log directory by command "mkdir /var/log/mail_av"
# you need install pwgen package for that via command "apt update && apt install pwgen"
# create unical policy name
pol=$(pwgen 10 -1 -s -0)
# create policy file
echo "FirstAction=Skip" > /var/log/mail_av/$pol.pol
echo "ScanMailBases=Yes" >> /var/log/mail_av/$pol.pol
echo "ScanPlainMail=Yes" >> /var/log/mail_av/$pol.pol
echo "UseAnalyzer=Yes" >> /var/log/mail_av/$pol.pol
echo "HeuristicLevel=Medium" >> /var/log/mail_av/$pol.pol
echo "[ScanScope.item_1]" >> /var/log/mail_av/$pol.pol
echo "Path=$2" >> /var/log/mail_av/$pol.pol
# create policy in KESL from file
/opt/kaspersky/kesl/bin/kesl-control --create-task $pol --type ODS --file /var/log/mail_av/$pol.pol >> /dev/null
# check file by KESL
vir=$(/opt/kaspersky/kesl/bin/kesl-control --start-task $pol -W|grep 'DetectName'|awk -F'=' '{print $2}'| head -1)
# remove policy from KESL
/opt/kaspersky/kesl/bin/kesl-control --delete-task $pol
# find virus name in KESL output
if [ -z $vir ]; then
rm -f /var/log/mail_av/$pol.pol
# write result to log that letter good
echo "Mail $2 was checked succesfull" >> /var/log/mail_av/checked
echo "v1"
echo "OK";
else
# write result to log that letter virused
# KESL policy don't delete
echo "In mail $2 find $vir" >> /var/log/mail_av/$pol.pol
echo "Mail $2 was blocked. More info in /var/log/mail_av/$pol.pol file" >> /var/log/mail_av/checked
echo "v1"
echo "VIRUS: $vir"
fi
exit 0PMG config file /etc/pmg/pmg.conf
Code:
section: admin
clamav 0
custom_check 1The output log when received mail
Code:
Oct 29 21:42:51 pmg pmg-smtp-filter[62541]: 2024/10/29-21:42:51 CONNECT TCP Peer: "[127.0.0.1]:34826" Local: "[127.0.0.1]:10024"
Oct 29 21:42:51 pmg pmg-smtp-filter[62541]: 120A756720F46B9621E: new mail message-id=<003a01db2a10$b1f13560$15d3a020$@sea.vn>
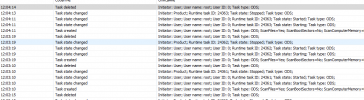
Oct 29 21:42:52 pmg pmg-smtp-filter[62541]: Task error. Creating tasks is blocked by policy
Oct 29 21:42:52 pmg pmg-smtp-filter[62541]: Invalid task ID. Task 'cUHaQHfTTf' not found
Oct 29 21:42:52 pmg pmg-smtp-filter[62541]: Invalid task ID. Task 'cUHaQHfTTf' not found
Oct 29 21:42:56 pmg pmg-smtp-filter[62541]: WARNING: check: dns_block_rule URIBL_BLOCKED hit, creating /root/.spamassassin/dnsblock_multi.uribl.com (This means DNSBL blocked you due to too many queries. Set all affected rules score to 0, or use "dns_query_restriction deny multi.uribl.com" to disable queries)
Oct 29 21:42:56 pmg pmg-smtp-filter[62541]: WARNING: check: dns_block_rule RCVD_IN_VALIDITY_SAFE_BLOCKED hit, creating /root/.spamassassin/dnsblock_sa-accredit.habeas.com (This means DNSBL blocked you due to too many queries. Set all affected rules score to 0, or use "dns_query_restriction deny sa-accredit.habeas.com" to disable queries)
Oct 29 21:42:56 pmg pmg-smtp-filter[62541]: WARNING: check: dns_block_rule RCVD_IN_VALIDITY_RPBL_BLOCKED hit, creating /root/.spamassassin/dnsblock_bl.score.senderscore.com (This means DNSBL blocked you due to too many queries. Set all affected rules score to 0, or use "dns_query_restriction deny bl.score.senderscore.com" to disable queries)
Oct 29 21:42:56 pmg pmg-smtp-filter[62541]: WARNING: check: dns_block_rule RCVD_IN_VALIDITY_CERTIFIED_BLOCKED hit, creating /root/.spamassassin/dnsblock_sa-trusted.bondedsender.org (This means DNSBL blocked you due to too many queries. Set all affected rules score to 0, or use "dns_query_restriction deny sa-trusted.bondedsender.org" to disable queries)
Oct 29 21:42:56 pmg pmg-smtp-filter[62541]: 120A756720F46B9621E: SA score=0/5 time=3.804 bayes=undefined autolearn=disabled hits=DKIM_INVALID(0.1),DKIM_SIGNED(0.1),DMARC_PASS(-0.1),HTML_MESSAGE(0.001),KAM_DMARC_STATUS(0.01),RCVD_IN_VALIDITY_CERTIFIED_BLOCKED(0.001),RCVD_IN_VALIDITY_RPBL_BLOCKED(0.001),RCVD_IN_VALIDITY_SAFE_BLOCKED(0.001),SPF_HELO_NONE(0.001),SPF_PASS(-0.001),URIBL_BLOCKED(0.001)
Oct 29 21:42:56 pmg postfix/smtpd[101185]: connect from localhost.localdomain[127.0.0.1]
Last edited:
Hi.Oct 29 21:42:52 pmg pmg-smtp-filter[62541]: Task error. Creating tasks is blocked by policy
Oct 29 21:42:52 pmg pmg-smtp-filter[62541]: Invalid task ID. Task 'cUHaQHfTTf' not found
Oct 29 21:42:52 pmg pmg-smtp-filter[62541]: Invalid task ID. Task 'cUHaQHfTTf' not found
As I can see, KESL can't create local task.
You must see KESL policy. If it works via KSC, you must allow create local tasks.
https://support.kaspersky.com/KES4Linux/11.4.0/en-US/233440.htm
Option "Allow users to view and manage local tasks" must be enabled.
Last edited:
Oh. It worked.Hi.
As I can see, KESL can't create local task.
You must see KESL policy. If it works via KSC, you must allow create local tasks.
https://support.kaspersky.com/KES4Linux/11.4.0/en-US/233440.htm
Option "Allow users to view and manage local tasks" must be enabled.
Thanks.