I was curious to see if something bad happens in my network if my password can be stolen , and i tested with mitm attack to spy https traffic i see that the password for login field in proxmox-frontend [pve / pam] is send in plain text to the backend.
Is argon2 or some hashing implemented or someone need to pull request it?
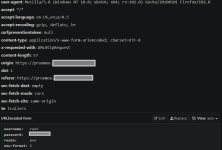
Is argon2 or some hashing implemented or someone need to pull request it?

Last edited:

