Hi,
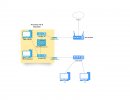
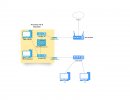
For the time being, I've installed pfSense in Proxmox as a VM. Here is the diagram:
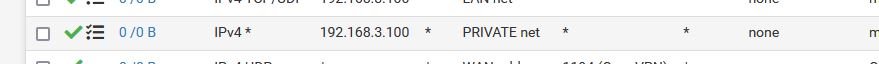
On NIC1 is my WAN connected to my ISP router in, say, DMZ
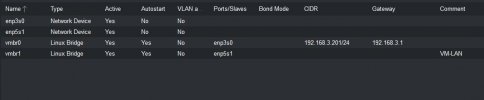
Here is my Proxmox network setup:
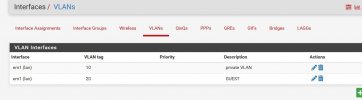
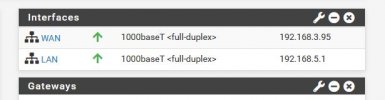
In pfSense the two virtual switch are seen this way:
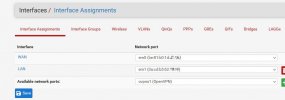
Basically the LAN above with IP 192.168.5.1 manages both Vms in Proxmox and any devices connected to the esternal physical swith on the NIC2.
Everything works greats BUT, for learning purpose, I'd like now to rearrange my network and create VLANs: VLAN10, VLAN20, and VLAN30.
VLAN10 for VMs in Proxmox, my desktop and my private WIFI. VLAN20 for my IoT, and VLAN30 for guest wifi and maybe for one ethernet port on the physical swith. I'm going to use a DD-WRT device to accomplish that. I think that I don't need to change any setup on my WAN port since I also want to access Proxmox from WAN port
Before going on I'd like to figure a few things out and make up my mind on the Proxmox side first.
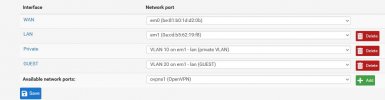
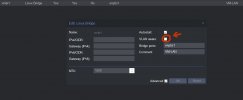
1) Should I enable 'Vlan aware' in Proxmox for the virtual switch vmbr1:
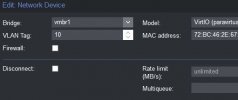
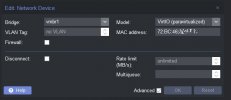
2) Do I need to set up VLAN tag for any VM here too (the windows VM in thie case below?
Please your thought and advice on my project.
Thanks
For the time being, I've installed pfSense in Proxmox as a VM. Here is the diagram:

On NIC1 is my WAN connected to my ISP router in, say, DMZ
Here is my Proxmox network setup:

In pfSense the two virtual switch are seen this way:


Basically the LAN above with IP 192.168.5.1 manages both Vms in Proxmox and any devices connected to the esternal physical swith on the NIC2.
Everything works greats BUT, for learning purpose, I'd like now to rearrange my network and create VLANs: VLAN10, VLAN20, and VLAN30.
VLAN10 for VMs in Proxmox, my desktop and my private WIFI. VLAN20 for my IoT, and VLAN30 for guest wifi and maybe for one ethernet port on the physical swith. I'm going to use a DD-WRT device to accomplish that. I think that I don't need to change any setup on my WAN port since I also want to access Proxmox from WAN port
Before going on I'd like to figure a few things out and make up my mind on the Proxmox side first.
1) Should I enable 'Vlan aware' in Proxmox for the virtual switch vmbr1:

2) Do I need to set up VLAN tag for any VM here too (the windows VM in thie case below?

Please your thought and advice on my project.
Thanks
Attachments
Last edited: