I am newbie w pfsense.
I've installed pfsense - it works well. Have 2 NICs - one for LAN (Public IP: x.x. 198.121) and one for WAN (Public IP: x.x.198.122). Both gateways are online. Traffic graph shows traffic on both interfaces and with right host IPs.
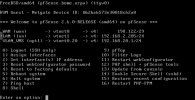
My VMs get via DHCP a LAN IP (something like192.168.2.x) but if I query their public Ip via
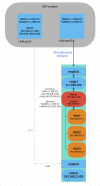
How do I route outbound VM traffic via WAN and incoming WAN traffic to a specific LAN IP 192.168.2.x?
I've installed pfsense - it works well. Have 2 NICs - one for LAN (Public IP: x.x. 198.121) and one for WAN (Public IP: x.x.198.122). Both gateways are online. Traffic graph shows traffic on both interfaces and with right host IPs.
My VMs get via DHCP a LAN IP (something like192.168.2.x) but if I query their public Ip via
host myip.opendns.com resolver1.opendns.com I get the LAN public IP. So my assumption is that it routes via LAN outbound.How do I route outbound VM traffic via WAN and incoming WAN traffic to a specific LAN IP 192.168.2.x?
Last edited: