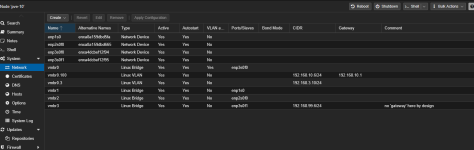
Hi,
I have OpenWRT in VM. I pass-through several hardware NICs including the one that is 'wan'. I also pass in one virtual bridge (vmbr1) which is part of 'lan' subnet. This way I can connect my other lxc or vm to 'lan'. I wanted to pass in second virtual bridge (vmbr2) for my second subnet 'sec'. But when I do that, all of the sudden my 'wan' stops working (doesn't get an ip) and thus I do not have internet conectivity and I can not use openWRT Luci interface.
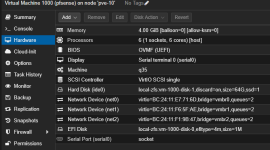
This is a screenshot of the devices added to the vm.
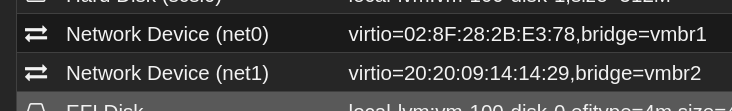
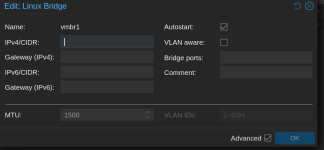
Any ideas what could be the issues? I tried to add the vmbr2 (which is eth4 in openwrt) to a brige for 'sec' (same config for vmbr1 and 'lan' bridge). But it didn't help. I also set manually mac addresses for each device because several had same. But it also didn't help. Both bridges (vmbr1 and 2) has the same config:
I have OpenWRT in VM. I pass-through several hardware NICs including the one that is 'wan'. I also pass in one virtual bridge (vmbr1) which is part of 'lan' subnet. This way I can connect my other lxc or vm to 'lan'. I wanted to pass in second virtual bridge (vmbr2) for my second subnet 'sec'. But when I do that, all of the sudden my 'wan' stops working (doesn't get an ip) and thus I do not have internet conectivity and I can not use openWRT Luci interface.
This is a screenshot of the devices added to the vm.

Any ideas what could be the issues? I tried to add the vmbr2 (which is eth4 in openwrt) to a brige for 'sec' (same config for vmbr1 and 'lan' bridge). But it didn't help. I also set manually mac addresses for each device because several had same. But it also didn't help. Both bridges (vmbr1 and 2) has the same config: