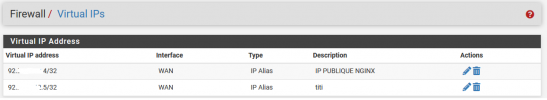
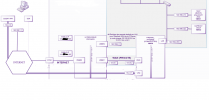
Hey all!
I've a PROXMOX server with many IP aliases on eth0 as eth0:0 , eth0:1, etc.
I installed a Pfsense on vmbr1 (considered as WAN with 10.0.0.x) and vmbr2 (considered as LAN with 192.168.9.x).
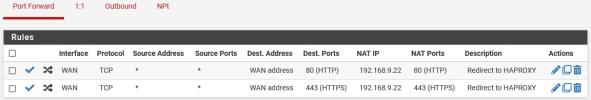
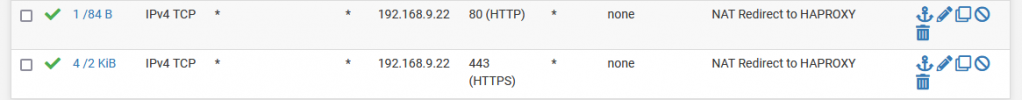
Everything is working fine for coming traffic from Internet: VM are accessible from outside, and responding with correct IP address.
Internet -> eth0 (or eth0:0, eth0:1, etc) to vmbr0 PROXMOX -> vmbr1 private Wan Pfsense (10.0.0.x) -> vmbr2 lan Pfsense (192.168.9.x) -> VM
BUT when a VM tries to go to outside world on Internet (ex: sending an email from a VM, etc.) then for this outgoing traffic ONLY the IP bare-metal server is used.
VM (ex:192.168.9.10) -> vmbr2 lan Pfsense (192.168.9.x) -> vmbr1 private Wan Pfsense (10.0.0.x) -> vmbr0 PROXMOX -> eth0 -> Internet (with eth0 IP ADDRESS)
I've no clue how to specify the outgoing IP address by selecting those from eth0:0, eth0:1, etc ????
I've searched in many way but didn't find the answer. Need to put entry in PROXMOX Firewall? What kind of entries? Another ideas??
Architecture is like this one: https://blog.zwindler.fr/2017/07/18/deploiement-de-proxmox-ve-5-sur-un-serveur-dedie-part-2/
Thanks for your feedback!
I've a PROXMOX server with many IP aliases on eth0 as eth0:0 , eth0:1, etc.
I installed a Pfsense on vmbr1 (considered as WAN with 10.0.0.x) and vmbr2 (considered as LAN with 192.168.9.x).
Everything is working fine for coming traffic from Internet: VM are accessible from outside, and responding with correct IP address.
Internet -> eth0 (or eth0:0, eth0:1, etc) to vmbr0 PROXMOX -> vmbr1 private Wan Pfsense (10.0.0.x) -> vmbr2 lan Pfsense (192.168.9.x) -> VM
BUT when a VM tries to go to outside world on Internet (ex: sending an email from a VM, etc.) then for this outgoing traffic ONLY the IP bare-metal server is used.
VM (ex:192.168.9.10) -> vmbr2 lan Pfsense (192.168.9.x) -> vmbr1 private Wan Pfsense (10.0.0.x) -> vmbr0 PROXMOX -> eth0 -> Internet (with eth0 IP ADDRESS)
I've no clue how to specify the outgoing IP address by selecting those from eth0:0, eth0:1, etc ????
I've searched in many way but didn't find the answer. Need to put entry in PROXMOX Firewall? What kind of entries? Another ideas??
Architecture is like this one: https://blog.zwindler.fr/2017/07/18/deploiement-de-proxmox-ve-5-sur-un-serveur-dedie-part-2/
Thanks for your feedback!
Last edited: