Hi all
I've got a general question. I'm new to OpenvSwitch. I have 3 proxmox servers in a cluster. I got openswitch installed on all of them. Each server has a bond of 2 network cards which I then connect to vmbr0. Everything works as excpected so far. Here is an example of a proxmox configuration:

When I use the vlan100 on VMs on the same host, they can talk to each other. If I setup the VMs on different hosts, they can't talk to each other. What would the correct way be to solve this?
1) Would I just need to make the physical switch have VLANs on the ports being used by the Proxmox hosts and also add trunks to the bond0?
2) Do I need to do this for all hosts in the cluster or is there a way to pass this info to all other hosts?
3) If I want the VMs to have access to the internet would you solve it with a virtual firewall (for example pfsense) or do this directly on the physical firewall?
4) When is GRE used and is it safe?
5) What would your recommended solution be?
This is a simple graphic of my setup:
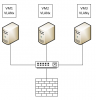
My goal would be for VM1 to be able to talk to VM2 and also have Internet access. VM3 for example should be isolated from the other 2 but also have internet access.
Thanks for your opinions and help!
silbro
I've got a general question. I'm new to OpenvSwitch. I have 3 proxmox servers in a cluster. I got openswitch installed on all of them. Each server has a bond of 2 network cards which I then connect to vmbr0. Everything works as excpected so far. Here is an example of a proxmox configuration:

When I use the vlan100 on VMs on the same host, they can talk to each other. If I setup the VMs on different hosts, they can't talk to each other. What would the correct way be to solve this?
1) Would I just need to make the physical switch have VLANs on the ports being used by the Proxmox hosts and also add trunks to the bond0?
2) Do I need to do this for all hosts in the cluster or is there a way to pass this info to all other hosts?
3) If I want the VMs to have access to the internet would you solve it with a virtual firewall (for example pfsense) or do this directly on the physical firewall?
4) When is GRE used and is it safe?
5) What would your recommended solution be?
This is a simple graphic of my setup:

My goal would be for VM1 to be able to talk to VM2 and also have Internet access. VM3 for example should be isolated from the other 2 but also have internet access.
Thanks for your opinions and help!
silbro

