Hi,
i get that "code: value may only be 1024 characters long." sometimes, it appears and disappears from time to time.
i get that "code: value may only be 1024 characters long." sometimes, it appears and disappears from time to time.
When can we expect the patch to be live?I've sent a patch increasing the limit to 2048 for now. This should fix the issues with Azure for the time being.
libpve-access-control release (7.2-4 or higher)./usr/share/perl5/PVE/API2/OpenId.pm and changing the limit for the `code` parameter in the `login` API call accordingly.__PACKAGE__->register_method ({
name => 'login',
path => 'login',
method => 'POST',
protected => 1,
description => " Verify OpenID authorization code and create a ticket.",
parameters => {
additionalProperties => 0,
properties => {
'state' => {
description => "OpenId state.",
type => 'string',
maxLength => 1024,
},So change the 1024 to 2048?The patch has been applied and will be part of the nextlibpve-access-control release(7.2-4 or higher).
If you want to manually change it until then, you can do so by editing/usr/share/perl5/PVE/API2/OpenId.pmand changing the limit for the `code` parameter in the `login` API call accordingly.
Code:__PACKAGE__->register_method ({ name => 'login', path => 'login', method => 'POST', protected => 1, description => " Verify OpenID authorization code and create a ticket.", parameters => { additionalProperties => 0, properties => { 'state' => { description => "OpenId state.", type => 'string', maxLength => 1024, },
pvedaemon and pveproxy with the following command:systemctl restart pvedaemon.service pveproxy.servicesystemctl status pvedaemon.service pveproxy.serviceThis might be a similar issue as in https://bugzilla.proxmox.com/show_bug.cgi?id=3916
The issue in the bug tracker is with lemonldap-ng.
Could you try downgradinglibpve-rs-perlto version 0.5.0?
my $info = $openid->verify_authorization_code($param->{code}, $private_auth_state);just FYI- it still does not work. I am on 7.3-6 (updated as of today). same exact error "Failed to contact token endpoint: Request failed"Packagelibpve-access-controlstarting from version 7.2-4 already contain the fix.
openid authentication failure; rhost=::ffff:192.168.2.4 msg=Failed to contact token endpoint: Request failed[02/Apr/2023:19:46:16 +0000] - 200 200 - POST https sso.internal.local"/webman/sso/SSOAccessToken.cgi" [Client 192.168.1.101] [Length 119] [Gzip -] [Sent-to 192.168.2.200] "Go-http-client/2.0" "-"
[02/Apr/2023:19:46:17 +0000] - 200 200 - GET https sso.internal.local"/webman/sso/SSOUserInfo.cgi" [Client 192.168.1.101] [Length 56] [Gzip -] [Sent-to 192.168.2.200] "Go-http-client/2.0" "-"[02/Apr/2023:19:46:22 +0000] - 200 200 - GET https sso.internal.local "/webman/sso/openid-jwks.json" [Client 192.168.1.101] [Length 435] [Gzip -] [Sent-to 192.168.2.200] "ureq/2.4.0" "-"
[02/Apr/2023:19:46:22 +0000] - 400 400 - POST https sso.internal.local "/webman/sso/SSOAccessToken.cgi" [Client 192.168.1.101] [Length 46] [Gzip -] [Sent-to 192.168.2.200] "ureq/2.4.0" "-"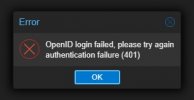
Updated to the latest version of everything, whole server restarted, AAD TenantId, ClientId and Client Secret checked and recreated, nothing worked..Just to be clear, has this package been moved to production version yet, because it still doesn't work?
We've got Linux [server name would be here] 5.15.64-1-pve #1 SMP PVE 5.15.64-1 (Thu, 13 Oct 2022 10:30:34 +0200) x86_64
pvedaemon[1489500]: openid authentication failure; rhost=::ffff:[ip address would be here] msg=Failed to contact token endpoint: Failed to parse server response
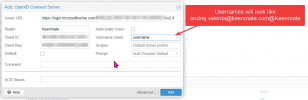
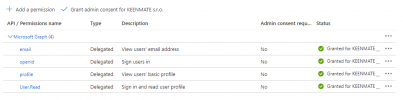
AAD app has proper permissions for email and profile, everything else is in default settings..
....
After reading your suggestion of updating the OpenId.pm script I have found out the problem is on this line
Perl:my $info = $openid->verify_authorization_code($param->{code}, $private_auth_state);
I tried changing the max allowed size to 4096 but it had not effect