Hello,
I recently upgraded to Proxmox VE 7.1-10 and am now receiving a 401 error when authenticating with Azure AD OpenID:
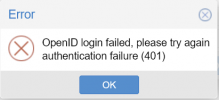
I am redirected to Microsoft and the Azure AD logs state that the authentication was successful. However, I cannot log in. This seems to be restricted to Azure AD as I have another instance using Keycloak and I can log in fine. I can only see the following line in /var/log/syslog:
Is there any other place where logs are stored and do you have any ideas what might be going on?
Thanks!
I recently upgraded to Proxmox VE 7.1-10 and am now receiving a 401 error when authenticating with Azure AD OpenID:

I am redirected to Microsoft and the Azure AD logs state that the authentication was successful. However, I cannot log in. This seems to be restricted to Azure AD as I have another instance using Keycloak and I can log in fine. I can only see the following line in /var/log/syslog:
pvedaemon[137919]: openid authentication failure; rhost=<redacted> msg=Failed to contact token endpoint: Request failedIs there any other place where logs are stored and do you have any ideas what might be going on?
Thanks!

