We are hosting multiple LXC containers on our dedicated servers (Debian 10). We are mainly hosting game servers and we noticed an oddly annoying pattern.
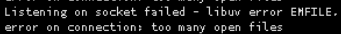
Our game servers get the following errors and shut down. It happens randomly and when there are most players on each servers.
and
How can we set the limit to a higher number for each lxc unprivileged container? We looked into other tutorials but we could not make it work. Does the container take in consideration the host for this as well? Do we need to increase the open file limit to the dedicated server OS and the lxc unprivileged container?
We have an experience of over 2 years using proxmox, but we mostly used the interface and have limited knowledge on the server side of things.
Our game servers get the following errors and shut down. It happens randomly and when there are most players on each servers.
Code:
terminate called after throwing an instance of 'boost::wrapexcept<boost::system::system_error>'
what(): boost::random_device: cannot open random-number pseudo-device /dev/urandom: No file descriptors availableand
How can we set the limit to a higher number for each lxc unprivileged container? We looked into other tutorials but we could not make it work. Does the container take in consideration the host for this as well? Do we need to increase the open file limit to the dedicated server OS and the lxc unprivileged container?
We have an experience of over 2 years using proxmox, but we mostly used the interface and have limited knowledge on the server side of things.