Argh.
I hate to add to the pile of permission related funk around PBS unprivileged lxc's trying to use a mounted USB drive from the proxmox host.
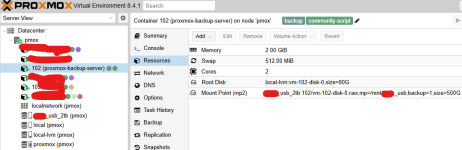
But I've got a usb drive mounted in my proxmox host, and configured as a mount point in the /etc/pve/lxc/xxx.conf file using the mp parameters.
While I can create files in the PBS server lxc as root, when I try to add the mountpoint as a datastore, I get the dreaded eperm.
So I realize I'm in the chronic flail of the nobody/nogroup mapping.
I don't even have a perfect question formulated, but I think basically I'm worn out re-reading and trying to compare dates and evaluate the quality of the threads and documentation out there...
I've seen numerous other people flail over this, and also see conflicting data about whether this can all be done through the gui or not, etc.
I am surprised there isn't a fresh FAQ on this in the PBS documentation, seems like it could make the cut... The doc related to unprivileged containers (see below) is 4 years untouched, and seems to at least be behind the news of gui functionality available since then.
It seems like the 'right' method is to do id mapping from the host to the lxc.
I've seen threads where adding uid/gid to the mp parameters are supposed to work and seem like a simple solution- but is that in the /etc/fstab for the proxmox host, or in the lxc config file where the mp is defined? I've gotten neither to work, can't see where the uid parameters are valid even though I've found multiple references to it, and seems like that would be easy...
I've also seen the rather convoluted id.mapping option threads, but I haven't actually tried it because it seems rather clunky, and it worries me that this document (unlike many related threads) seems to be 4 years old (see below).
https://pve.proxmox.com/mediawiki/index.php?title=Unprivileged_LXC_containers&action=history
I also feel like I've found so many conflicting 'solutions' that my head's a little dizzy; is that the latest and greatest doc about this topic? Is there another better source of truth on best practice / simple solution?
So all that said, I'm not proud of this post, but I feel like I've gone through this and around and around for a couple days now, and am not trusting the data sources I keep re-reading.
If anybody can point at the most current 'source of truth' on how to do this most properly (i.e., not by giving the container privileges, etc), that would be great.
It seems pretty whacky that I can so easily have the storage available to the container, and that the container root can create files on it, but it's a multi day crazy hunt to figure out how to allow a different local user to have access as the pbs server user.
Thanks for reading, sorry for this, but I know I'm not alone in flailing through it.
I hate to add to the pile of permission related funk around PBS unprivileged lxc's trying to use a mounted USB drive from the proxmox host.
But I've got a usb drive mounted in my proxmox host, and configured as a mount point in the /etc/pve/lxc/xxx.conf file using the mp parameters.
While I can create files in the PBS server lxc as root, when I try to add the mountpoint as a datastore, I get the dreaded eperm.
So I realize I'm in the chronic flail of the nobody/nogroup mapping.
I don't even have a perfect question formulated, but I think basically I'm worn out re-reading and trying to compare dates and evaluate the quality of the threads and documentation out there...
I've seen numerous other people flail over this, and also see conflicting data about whether this can all be done through the gui or not, etc.
I am surprised there isn't a fresh FAQ on this in the PBS documentation, seems like it could make the cut... The doc related to unprivileged containers (see below) is 4 years untouched, and seems to at least be behind the news of gui functionality available since then.
It seems like the 'right' method is to do id mapping from the host to the lxc.
I've seen threads where adding uid/gid to the mp parameters are supposed to work and seem like a simple solution- but is that in the /etc/fstab for the proxmox host, or in the lxc config file where the mp is defined? I've gotten neither to work, can't see where the uid parameters are valid even though I've found multiple references to it, and seems like that would be easy...
I've also seen the rather convoluted id.mapping option threads, but I haven't actually tried it because it seems rather clunky, and it worries me that this document (unlike many related threads) seems to be 4 years old (see below).
https://pve.proxmox.com/mediawiki/index.php?title=Unprivileged_LXC_containers&action=history
I also feel like I've found so many conflicting 'solutions' that my head's a little dizzy; is that the latest and greatest doc about this topic? Is there another better source of truth on best practice / simple solution?
So all that said, I'm not proud of this post, but I feel like I've gone through this and around and around for a couple days now, and am not trusting the data sources I keep re-reading.
If anybody can point at the most current 'source of truth' on how to do this most properly (i.e., not by giving the container privileges, etc), that would be great.
It seems pretty whacky that I can so easily have the storage available to the container, and that the container root can create files on it, but it's a multi day crazy hunt to figure out how to allow a different local user to have access as the pbs server user.
Thanks for reading, sorry for this, but I know I'm not alone in flailing through it.