Dear at all,
i have some questions regarding built up an offsite Backup with 2 PBS.
I have made an small drawing of the setup idea.
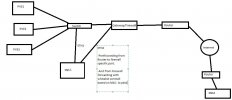
ETH2 should be only used for syncing between PBS1 and PBS2.
ETH2 is planed to put in an seperate Network to make it more difficult to enter the main Network which is connected on ETH1.
ETH1 is used for doing the backups from the PVE-Nodes.
Is PBS by default safe on the interface ETH2?
Or i must do my own firewall rules on the pbs1 for eth2?
If yes, is it enough to do?
port is correct for doing remote and syncing?
On the baremetal-firewall/gateway i would like to do any further allowance rule. Like only one special ip adress is allowed to enter.
But the problem is that pbs2 has no static ip. Which rule possibility i have more? MAC of the ETH from PBS2?
Is this setup safe?
Or you would suggest another setup.
many thanks
best regards
thomas
i have some questions regarding built up an offsite Backup with 2 PBS.
I have made an small drawing of the setup idea.

ETH2 should be only used for syncing between PBS1 and PBS2.
ETH2 is planed to put in an seperate Network to make it more difficult to enter the main Network which is connected on ETH1.
ETH1 is used for doing the backups from the PVE-Nodes.
Is PBS by default safe on the interface ETH2?
Or i must do my own firewall rules on the pbs1 for eth2?
If yes, is it enough to do?
ufw deny all incoming eth2
ufw allow in on eth2 to any port 8007/tcpport is correct for doing remote and syncing?
On the baremetal-firewall/gateway i would like to do any further allowance rule. Like only one special ip adress is allowed to enter.
But the problem is that pbs2 has no static ip. Which rule possibility i have more? MAC of the ETH from PBS2?
Is this setup safe?
Or you would suggest another setup.
many thanks
best regards
thomas

