Hello!
I love the idea of SDNs on Proxmox Cluster. I believe that SDNs will evolve fast.
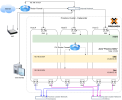
After trying some solutions to optimize my usage of Proxmox SDNs and improve the flexibility and security of my environment, I've decided to implement a solution based on the two routers-firewalls concept, also known as North-South + East-West implementation. With this architecture, I intend to use SDNs to segment my network and make implementation easy, but also have access to all features that a dedicated router/firewall solution has available.
The idea is simple: North-South Router/Firewall will take care of external (Internet/WAN) to internal network (local). East-West will handle internal traffic and network segmentation. Besides the fact that there are more appliances to manage, this architecture has some advantages:
The final architecture is like this:
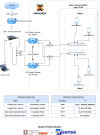
My option for master-backup solution intends to guarantee a service 100% disponible. For most use cases, especially when you are not using a Proxmox Cluster, a single EW-router will be good enough.
Some requirements of my architecture:
1 – As a starting point, everyone can talk to everyone. It means that a user on Internal Network has access to VMs on VNet Y or VNet X and vice-versa.
2 – No NAT. Internal traffic must use the machine's IP without any kind of translation.
3 – Block private networks and block bogon networks must be disable on EW-router Internal Network (WAN) interface.
4 – Changes to the NS–router must be minimized. I decided to route back a larger subnet (/17) and use smaller subnets (/24) to my VNets.
5 – Blocks must be implemented by firewall rules on EW-router. Example: for cloudflared public exposed network, I'd added a block Internal Network rule on this interface.
I'm a PFSense user, but I decided to test OpenSense to implement EW-router. The master-backup solution was implemented following this guide: Don't Use A Firewall, Use 2! OpnSense High Availability Guide (youtube.com)

If you need more details or even a step-by-step guide about how to implement this architecture, please, leave a reply here and I will do my best to help.
I love the idea of SDNs on Proxmox Cluster. I believe that SDNs will evolve fast.
After trying some solutions to optimize my usage of Proxmox SDNs and improve the flexibility and security of my environment, I've decided to implement a solution based on the two routers-firewalls concept, also known as North-South + East-West implementation. With this architecture, I intend to use SDNs to segment my network and make implementation easy, but also have access to all features that a dedicated router/firewall solution has available.
The idea is simple: North-South Router/Firewall will take care of external (Internet/WAN) to internal network (local). East-West will handle internal traffic and network segmentation. Besides the fact that there are more appliances to manage, this architecture has some advantages:
- attacks will affect just one appliance, reducing effects and making diagnostics faster.
- changes on EW-router will not affect internal users connection with internet.
- ownership of NS-router and ES-router is not necessarily the same. Example: Security Team can be owner of NS-router and Infrastructure Team owns the ES-router.
- Proxmox SDNs will be managed and protected by recognized router and firewall solutions that will add value to the final architecture, especially for small and medium business implementations.
The final architecture is like this:

My option for master-backup solution intends to guarantee a service 100% disponible. For most use cases, especially when you are not using a Proxmox Cluster, a single EW-router will be good enough.
Some requirements of my architecture:
1 – As a starting point, everyone can talk to everyone. It means that a user on Internal Network has access to VMs on VNet Y or VNet X and vice-versa.
2 – No NAT. Internal traffic must use the machine's IP without any kind of translation.
3 – Block private networks and block bogon networks must be disable on EW-router Internal Network (WAN) interface.
4 – Changes to the NS–router must be minimized. I decided to route back a larger subnet (/17) and use smaller subnets (/24) to my VNets.
5 – Blocks must be implemented by firewall rules on EW-router. Example: for cloudflared public exposed network, I'd added a block Internal Network rule on this interface.
I'm a PFSense user, but I decided to test OpenSense to implement EW-router. The master-backup solution was implemented following this guide: Don't Use A Firewall, Use 2! OpnSense High Availability Guide (youtube.com)

If you need more details or even a step-by-step guide about how to implement this architecture, please, leave a reply here and I will do my best to help.