Probably already a few posts about this.
I am trying to mount an NFS drive to an unprivileged container. When trying to do so, I get this error:
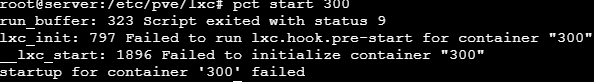
My configurations looks like this:
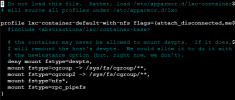
and
Many of the Xs are correct, verified them three different times while comparing with a Stack Exchange post and this Blog post.
Any ideas what I could possibly be doing wrong?
I am trying to mount an NFS drive to an unprivileged container. When trying to do so, I get this error:

My configurations looks like this:

and
arch: amd64
cores: 1
cpuunits: 512
hostname: XXXXXXXXX
memory: 512
mp0: XXX.XXX.XX.XX:/XXXXX,mp=/home/XXXXXXXXX/XXXXXX
net0: name=eth0,bridge=vmbr0,firewall=1,hwaddr=XX:XX:XX:XX:XX:XX,typ$
ostype: debian
rootfs: services:vm-300-disk-0,size=8G
swap: 512
unprivileged: 1
lxc.apparmor.profile: lxc-container-default-with-nfs
Many of the Xs are correct, verified them three different times while comparing with a Stack Exchange post and this Blog post.
Any ideas what I could possibly be doing wrong?

