I'm a newbie to Linux management (I've been doing low level (macOS) Unix for years, so I'm not totally new to unix-like stuff) as well as managing my own virtualisation setup. I am reading, searching and learning while setting up my new server environment on an Intel NUC with PVE and Ubuntu clients. My apologies for the long post/questions but I thought it best to give as much information to prevent a lot of misunderstandings.
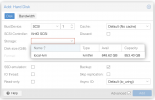
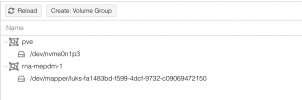
So, far I've been able to install PVE and setup an initial Ubuntu client, purely on the internal NVMe of the NUC. I've also been able to add a USB RAID enclosure and have it encrypted and mounted (at boot) in PVE's Debian. That means that my block devices now look like this:
So, I've reached my first goal: run PVE with a Ubuntu client and make sure all data is encrypted when the system is turned off (data protection against hardware theft). When the NUC boots I need to enter a hardware password (twice, once for the NUC, once for the internal SSD) then everything boots. As I have set up LUKS on PVE's Debian, I do not have to mess around with disk encryption on each client OS, so far so good.
My next goal is to (create and) mount a 500GB volume from PVE's /dev/sda on the Ubuntu client and make sure that the external data volume is backed up to the internal disk I will add remote backup later). Step one is creating the volume and having it mounted on the Ubuntu client. I assume my steps are to create a VG in PVE, create a LVM and have that mounted as a 'data' volume in the Ubuntu client OS by adding the volume as a 'hard disk' to the VM in PVE.
I am getting stuck because of my unfamiliarity with the toolset, so I have a couple of simple questions that show my ignorance and I could need some help/tips with. These are:
So, far I've been able to install PVE and setup an initial Ubuntu client, purely on the internal NVMe of the NUC. I've also been able to add a USB RAID enclosure and have it encrypted and mounted (at boot) in PVE's Debian. That means that my block devices now look like this:
Code:
root@pve:~# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 1.7T 0 disk
└─sda1 8:1 0 1.7T 0 part
└─luks-fa1483bd-f599-4dcf-9732-c09069472150 253:7 0 1.7T 0 crypt /mnt/RNAStore4
nvme0n1 259:0 0 931.5G 0 disk
├─nvme0n1p1 259:1 0 1007K 0 part
├─nvme0n1p2 259:2 0 512M 0 part /boot/efi
└─nvme0n1p3 259:3 0 931G 0 part
├─pve-swap 253:0 0 8G 0 lvm [SWAP]
├─pve-root 253:1 0 96G 0 lvm /
├─pve-data_tmeta 253:2 0 8.1G 0 lvm
│ └─pve-data-tpool 253:4 0 794.8G 0 lvm
│ ├─pve-data 253:5 0 794.8G 1 lvm
│ └─pve-vm--100--disk--0 253:6 0 32G 0 lvm
└─pve-data_tdata 253:3 0 794.8G 0 lvm
└─pve-data-tpool 253:4 0 794.8G 0 lvm
├─pve-data 253:5 0 794.8G 1 lvm
└─pve-vm--100--disk--0 253:6 0 32G 0 lvmSo, I've reached my first goal: run PVE with a Ubuntu client and make sure all data is encrypted when the system is turned off (data protection against hardware theft). When the NUC boots I need to enter a hardware password (twice, once for the NUC, once for the internal SSD) then everything boots. As I have set up LUKS on PVE's Debian, I do not have to mess around with disk encryption on each client OS, so far so good.
My next goal is to (create and) mount a 500GB volume from PVE's /dev/sda on the Ubuntu client and make sure that the external data volume is backed up to the internal disk I will add remote backup later). Step one is creating the volume and having it mounted on the Ubuntu client. I assume my steps are to create a VG in PVE, create a LVM and have that mounted as a 'data' volume in the Ubuntu client OS by adding the volume as a 'hard disk' to the VM in PVE.
I am getting stuck because of my unfamiliarity with the toolset, so I have a couple of simple questions that show my ignorance and I could need some help/tips with. These are:
- How much of this stuff can I do in the PVE GUI? Should I assume the GUI is no use for my stuff and do everything in the underlying Debian CLI? The whole LUKS stuff for the external RAID I did in the CLI on PVE's Debian. Should I avoid the GUI or can it make life simpler for me yet??
- PVE Install created an LVM of 100GB and a LVM-thin of 900GB
As I understand it, 'nvme0n1p3' is a partition and that is the same as a physical volume (PV). PVE's Debian has a single volume group (VG) called 'pve' that is made up of that single PV. And VG 'pve' contains two logical volumes, a standard one of 100GB that is called 'root' and a thin one that is called 'data'. The PVE installer has put the Ubuntu ISO on 'LVM:root' and the Ubuntu install created a bootable 32GB VM ('vm-100-disk-0') image from it on 'LVM-Thin:data'. I have two questions (and one unrelated third):Code:root@pve:~# lvs LV VG Attr LSize Pool Origin Data% Meta% Move Log Cpy%Sync Convert data pve twi-aotz-- <794.79g 0.56 0.26 root pve -wi-ao---- 96.00g swap pve -wi-ao---- 8.00g vm-100-disk-0 pve Vwi-a-tz-- 32.00g data 13.83- How do I create a VG on /dev/mapper/luks-fa1483bd-f599-4dcf-9732-c09069472150? Create a VG, add /dev/mapper/luks-fa1483bd-f599-4dcf-9732-c09069472150 or /dev/dm-7 to it as PV? Something is not right here, as I have created an ext4 file system on that device and I need it as block device. So, I must stop mounting it in PVE's Debian, I guess and adding /dev/mapper/luks-fa1483bd-f599-4dcf-9732-c09069472150 to the new VG will wipe that file system, correct?
- If I have a VG on /dev/mapper/luks-fa1483bd-f599-4dcf-9732-c09069472150, I should be able create a 500GB logical volume in it. What escapes me still is how I then in Ubuntu client OS mount that logical volume.
- Because I have a file system on the LUKS-encrypted external drive I could perform a small write speed test:
But I wonder, is this a reasonable test?Code:root@pve:~# dd if=/dev/zero of=/mnt/RNAStore4/tempfile bs=128k count=32k 32768+0 records in 32768+0 records out 4294967296 bytes (4.3 GB, 4.0 GiB) copied, 4.72204 s, 910 MB/s
Last edited: