Network has been lost after container restoration from backup.
Container OS: RockyLinux 9
Steps:
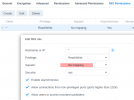
Restore container from backup on NFS.
No IP address on interface after start.
ifcfg-eth file with needed configuration is in place.
The probable reason i can see is UUID in the file is different from UUID reported by nmcli connection.
So i assume this happens. After container restore interface UUID is changed somehow and current ifcfg file does not reflect this situation.
If i delete and recreate interface from Proxmox GUI it creates interface with same (old) UUID and hence still no network.
Trying to change UUID to the value reported by nmcli and restarting NetworkManager but no luck. Still unconfigured interface.
The only workaround i found is to delete interface from Proxmox GUI, then delete ifcfg file. And recreate interface back.
This way container got its IP and such. It has new UUID of net in ifcfg file. But it is different from UUID reported by nmcli connection. So it is working until next restart.
After restart, container again looses network because interface became unconfigured again.
Hope i describe this clearly.
How can this be solved?
Container OS: RockyLinux 9
Steps:
Restore container from backup on NFS.
No IP address on interface after start.
ifcfg-eth file with needed configuration is in place.
The probable reason i can see is UUID in the file is different from UUID reported by nmcli connection.
So i assume this happens. After container restore interface UUID is changed somehow and current ifcfg file does not reflect this situation.
If i delete and recreate interface from Proxmox GUI it creates interface with same (old) UUID and hence still no network.
Trying to change UUID to the value reported by nmcli and restarting NetworkManager but no luck. Still unconfigured interface.
The only workaround i found is to delete interface from Proxmox GUI, then delete ifcfg file. And recreate interface back.
This way container got its IP and such. It has new UUID of net in ifcfg file. But it is different from UUID reported by nmcli connection. So it is working until next restart.
After restart, container again looses network because interface became unconfigured again.
Hope i describe this clearly.
How can this be solved?
Last edited: