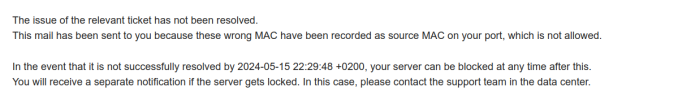
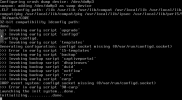
Thank you for your reply.Debug it step by step...
Run a ping from your VM to the outside world. Now check where it gets lost. On the host, sniff traffic on the bridge that your VM is connected to, to see if the correct MAC for that IP shows up or not. If it reaches the bridge, you can be sure, that the problem is on host or network-level.
Code:tcpdump -i vmbr0 ether host xx:xx:xx:xx:xx:xx
I was leaning towards either a sysctl setting, but maybe it's just the Proxmox VE Firewall and their "Security Group Policies" defined on Datacenter Level, applied on VM Level, yet ONLY showing on NODE level, without ANY indication whether the traffic was DROPPED or ACCEPTED: https://forum.proxmox.com/threads/p...ups-and-impossible-to-understand-logs.147404/
I also asked on the OPNSense Forum to see if they had a clue, if that maybe was intended behavior.
https://forum.opnsense.org/index.php?topic=40585.0
Come to think of it, I recently moved some of the VM Rules towards the "Group Security Policy" in Datacenter, then "loaded" the "Group Security Policy" into the VM. I thought it was maybe a sysctl change that did that, but since then ... no logs inside the VM Firewall Logs, ONLY on NODE level.
EDIT 1: running your command I can see a ton of UDP OpenVPN Traffic (at least that !), but nothing about ping/ICMP. I now added EXPLICITELY a "DIRECT" ICMP IN/OUT Rule (not using this "Security Group") to see if that fixes it (after rebooting the VM).
EDIT 2: Rebooted the OPNSense VM, tried to ping again. NOTHING. tcpdump register lots of ICMP going TO the OPNSense VM, but if I try to pin 8.8.8.8, run tcpdump, register everything, then look for 8.8.8.8, nothing is found
Heck I cannot even piung the hetzner gateway for some reason
It's like everything is reversed. INBOUND everything (or at least most stuff) works, OUTBOUND everything is broken
EDIT 3: I tried to run brct vmbr0 setageing 0 and the System "Crashed" (I had to issue a reboot from Hetzner Robot)
Nope, I'd probably be locked out of the Server if I did that. I did another attempt with
brctl setageing vmbr0 0 but it would just hang ....EDIT 4: this is getting ridicolous ... I can ping the OpenVPN Client I'm connecting from (Home) from the OPNSense VM. But I cannot ping the Gateway / DHCP Server I'm connected to, even though ... I could get an IP Address
EDIT 5: Not sure if applicable here, but I have NOT bound the Firewall Rules to any Interfaces. According to https://forum.proxmox.com/threads/v...tgoing-internet-connection.51542/#post-239172 it might be required (although in that case it's for a Routed Setup / NAT most likely).
And Hetzner is quite special with their Network Configuration, especially on the Host:
https://docs.hetzner.com/robot/dedi...fig-debian-ubuntu/#etcnetworkinterfaces-eni-1
Proxmox VE Host has this weird 255.255.255.255 or /32 Netmask with the pointopoint Setting.
Whereas the OPNSense VM gets via DHCP the /26 Subnet IP Address ...
EDIT 6: This is the latest /etc/network/interfaces for the affected Interfaces
Code:
auto lo
iface lo inet loopback
iface eth0 inet manual
auto vmbr0
iface vmbr0 inet static
hwaddress XX:XX:XX:XX:XX:XX
address xxx.xxx.xxx.proxmox
netmask 255.255.255.255
gateway xxx.xxx.xxx.gateway
pointopoint xxx.xxx.xxx.gateway
bridge-ports eth0
bridge-stp off
bridge_waitport 0
bridge-fd 0
bridge-disable-mac-learning 1
bridge-unicast-flood off
bridge-multicast-flood off
bridge-vlan-aware yes
bridge-vids 2-4096
pre-up ip addr flush dev eth0
post-up ip addr flush dev eth0
Last edited: