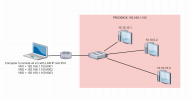
Nat port and remote vm inside LAN
- Thread starter phungvuong
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Hello,
how do you want to connect to your VMs? Via RDP, or SSH?
Ports are not just 'subgroups of IP addresses', they work on a different network layer.
So if you think that instead of 'aaa.bbb.ccc.ddd' you can input 'aaa.bbb.ccc.ddd:9001' in all your favourite programs then that won't in general.
Kind regards,
Benedikt
how do you want to connect to your VMs? Via RDP, or SSH?
Ports are not just 'subgroups of IP addresses', they work on a different network layer.
So if you think that instead of 'aaa.bbb.ccc.ddd' you can input 'aaa.bbb.ccc.ddd:9001' in all your favourite programs then that won't in general.
Kind regards,
Benedikt
Thanks for your reply.Hello,
how do you want to connect to your VMs? Via RDP, or SSH?
Ports are not just 'subgroups of IP addresses', they work on a different network layer.
So if you think that instead of 'aaa.bbb.ccc.ddd' you can input 'aaa.bbb.ccc.ddd:9001' in all your favourite programs then that won't in general.
Kind regards,
Benedikt
I want to connect to VMs via RDP.
I have 10 home server, one LAN IP for each server, every server i create 4 VMs inside and set nat ip for VMs. I want to remote VMs using server LAN IP : Port.
I have this NAT config but only VMs can ping to other computer in LAN and other computer outside VMs can't ping to VM
Code:
auto lo
iface lo inet loopback
iface enp5s0 inet manual
auto vmbr0
iface vmbr0 inet static
address 192.168.12.105/24
gateway 192.168.12.1
bridge-ports enp5s0
bridge-stp off
bridge-fd 0
auto vmbr2
iface vmbr2 inet static
address 10.10.10.254
netmask 255.255.255.0
bridge_ports none
bridge_stp off
bridge_fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.10.10.0/24' -o vmbr0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.10.10.0/24' -o vmbr0 -j MASQUERADE
post-up iptables -t nat -A PREROUTING -i vmbr0 -p tcp –dport 9001 -j DNAT –to 10.10.10.1:3389
post-down iptables -t nat -D PREROUTING -i vmbr0 -p tcp –dport 9001 -j DNAT –to 10.10.10.1:3389
post-up iptables -t nat -A PREROUTING -i vmbr0 -p tcp –dport 9002 -j DNAT –to 10.10.10.2:3389
post-down iptables -t nat -D PREROUTING -i vmbr0 -p tcp –dport 9002 -j DNAT –to 10.10.10.2:3389
post-up iptables -t nat -A PREROUTING -i vmbr0 -p tcp –dport 9003 -j DNAT –to 10.10.10.3:3389
post-down iptables -t nat -D PREROUTING -i vmbr0 -p tcp –dport 9003 -j DNAT –to 10.10.10.3:3389
post-up iptables -t nat -A PREROUTING -i vmbr0 -p tcp –dport 9004 -j DNAT –to 10.10.10.4:3389
post-down iptables -t nat -D PREROUTING -i vmbr0 -p tcp –dport 9004 -j DNAT –to 10.10.10.4:3389
Last edited:
The config looks good so far, although the IPs do not match your picture above. From the 192.168.12.0/24 subnet you should be able to RDP to 192.168.12.105:9001 - 192.168.12.105:9004 and reach your VMs that way.
It is quite normal that you can't ping your VMs from outside, since that happens on a different layer. Your port forwardings do not apply to pings. Pinging inside -> outside works because of your Masquerade rule, but pinging outside -> inside won't work.
It is quite normal that you can't ping your VMs from outside, since that happens on a different layer. Your port forwardings do not apply to pings. Pinging inside -> outside works because of your Masquerade rule, but pinging outside -> inside won't work.
I had change to correct ip but can not remote to VMs. also enable Remote Desktop and disable Firewall in VMs.The config looks good so far, although the IPs do not match your picture above. From the 192.168.12.0/24 subnet you should be able to RDP to 192.168.12.105:9001 - 192.168.12.105:9004 and reach your VMs that way.
It is quite normal that you can't ping your VMs from outside, since that happens on a different layer. Your port forwardings do not apply to pings. Pinging inside -> outside works because of your Masquerade rule, but pinging outside -> inside won't work.
I'm trying to do the same thing, but from the 192.168.10.0/24 subnet I cannot rdp to 192.168.10.50:9001 (which should target the VM with 10.10.10.1 on vmbr1).. Can anyone help?
Do I need to activate the firewall? (atm disabled at datacenter level)
Bash:
iface enp57s0 inet manual
auto vmbr0
iface vmbr0 inet static
address 192.168.10.50/24
gateway 192.168.10.1
bridge-ports enp57s0
bridge-stp off
bridge-fd 0
auto vmbr1
iface vmbr1 inet static
address 10.10.10.254
netmask 255.255.255.0
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.10.10.0/24' -o vmbr0 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.10.10.0/24' -o vmbr0 -j MASQUERADE
post-up iptables -t nat -A PREROUTING -i vmbr0 -p tcp –dport 9001 -j DNAT –to 10.10.10.1:3389
post-down iptables -t nat -D PREROUTING -i vmbr0 -p tcp –dport 9001 -j DNAT –to 10.10.10.1:3389
post-up iptables -t nat -A PREROUTING -i vmbr0 -p tcp –dport 9002 -j DNAT –to 10.10.10.2:3389
post-down iptables -t nat -D PREROUTING -i vmbr0 -p tcp –dport 9002 -j DNAT –to 10.10.10.2:3389
post-up iptables -t nat -A PREROUTING -i vmbr0 -p tcp –dport 9003 -j DNAT –to 10.10.10.3:3389
post-down iptables -t nat -D PREROUTING -i vmbr0 -p tcp –dport 9003 -j DNAT –to 10.10.10.3:3389
post-up iptables -t nat -A PREROUTING -i vmbr0 -p tcp –dport 9004 -j DNAT –to 10.10.10.4:3389
post-down iptables -t nat -D PREROUTING -i vmbr0 -p tcp –dport 9004 -j DNAT –to 10.10.10.4:3389
source /etc/network/interfaces.d/*Do I need to activate the firewall? (atm disabled at datacenter level)
Last edited: