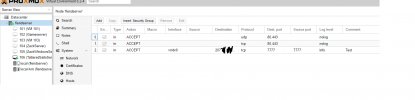
I'm running into a issue with proxmox firewalls.
I turned on the firewall on the datacenter,node, and vm side of things and created a port accept on incoming to 8006. I also have a bridge vmbr0 to eno1 to a public ip.
I also have a vmbr1 ip of 192.168.10.0/24 gateway of 192.168.10.100. I use.175 for my
Vm. I'm not able to access the Internet on that vm at all even I accepted port 80,443 on each layer.
Maybe I am misunderstanding something on it. Do I need to nat the private ip or do I need to add the destination to the firewall rules?
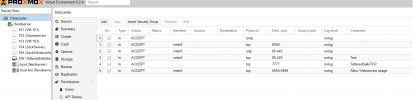
I turned on the firewall on the datacenter,node, and vm side of things and created a port accept on incoming to 8006. I also have a bridge vmbr0 to eno1 to a public ip.
I also have a vmbr1 ip of 192.168.10.0/24 gateway of 192.168.10.100. I use.175 for my
Vm. I'm not able to access the Internet on that vm at all even I accepted port 80,443 on each layer.
Maybe I am misunderstanding something on it. Do I need to nat the private ip or do I need to add the destination to the firewall rules?