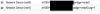Hi Forum
I have following scenario:
Got assigned multiple IPs (with different gateways) on the only one physical NIC on my Host system. All IPs but one reserved for the access to the Proxmox Host would be assigned to a Firewall VM. Only this firewall would interface with he host. The rest of the VMs would just get ips of the vlan from the Firewall VM over dhcp and also the FW VM would handle all the traffic and NATing and filtering. I struggle to configure this setup.
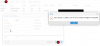
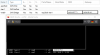
My (naive) idea was to create IPless Linux bridge to the primary Network device of the host. Conect the virtual NIC of the Firewall to that bridge. Create an ipless VLAN and connect other VMs NICs to the VLAN. The Firewall would have defined multiple IPs on its NIC and also distribute LAN IPs over DHCP and handle all the access of the VMs to the outside. Obviously my scenario is not possible (as the GUI won't allow me to do this) or I cannot set it up properly.
Could you point me into right direction to achieve what I want?
I have following scenario:
Got assigned multiple IPs (with different gateways) on the only one physical NIC on my Host system. All IPs but one reserved for the access to the Proxmox Host would be assigned to a Firewall VM. Only this firewall would interface with he host. The rest of the VMs would just get ips of the vlan from the Firewall VM over dhcp and also the FW VM would handle all the traffic and NATing and filtering. I struggle to configure this setup.
My (naive) idea was to create IPless Linux bridge to the primary Network device of the host. Conect the virtual NIC of the Firewall to that bridge. Create an ipless VLAN and connect other VMs NICs to the VLAN. The Firewall would have defined multiple IPs on its NIC and also distribute LAN IPs over DHCP and handle all the access of the VMs to the outside. Obviously my scenario is not possible (as the GUI won't allow me to do this) or I cannot set it up properly.
Could you point me into right direction to achieve what I want?