Hi,
Here we go again
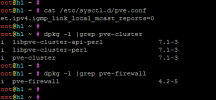
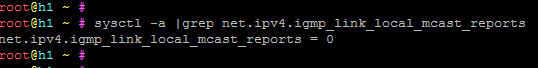
We are using Proxmox 7.1-8 and got an abuse message from Hetzner today:
Anyone else got the abuse message for Proxmox 7? Any ideas how to fix it?
Here we go again
We are using Proxmox 7.1-8 and got an abuse message from Hetzner today:
Abuse Message [AbuseID:the_ip]: MAC-Errors: MAC-Report for #server_id(server_ip)
Kontaktfoto
From network-abuse@hetzner.com on 2021-12-24 13:06
Detaljer
Abuse Message 9B839A1A.txt
(~194 B)
Dear Mr xxxxx,
We have detected that your server is using different MAC addresses from those allowed by your Robot account.
Anyone else got the abuse message for Proxmox 7? Any ideas how to fix it?