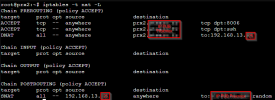
Chain PREROUTING (policy ACCEPT 6262 packets, 415K bytes)
num pkts bytes target prot opt in out source destination
1 67 3484 ACCEPT tcp -- * * 0.0.0.0/0 IP_PUB tcp dpt:8006
2 1 60 ACCEPT tcp -- * * 0.0.0.0/0 IP_PUB tcp dpt:22
3 846 35435 DNAT all -- * * 0.0.0.0/0 IP_PUB to:IP_WAN_OPNSENSE
Chain INPUT (policy ACCEPT 67 packets, 3484 bytes)
num pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 557 packets, 36008 bytes)
num pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 5082 packets, 307K bytes)
num pkts bytes target prot opt in out source destination
1 533 37395 SNAT all -- * * IP_WAN_OPNSENSE 0.0.0.0/0 to:IP_PUB random
root@prx2:~# iptables -L -n -v --line-numbers
Chain INPUT (policy ACCEPT 13 packets, 676 bytes)
num pkts bytes target prot opt in out source destination
1 47525 15M PVEFW-INPUT all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 2602 packets, 172K bytes)
num pkts bytes target prot opt in out source destination
1 155K 113M PVEFW-FORWARD all -- * * 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT (policy ACCEPT 94 packets, 6124 bytes)
num pkts bytes target prot opt in out source destination
1 48140 21M PVEFW-OUTPUT all -- * * 0.0.0.0/0 0.0.0.0/0
Chain PVEFW-Drop (1 references)
num pkts bytes target prot opt in out source destination
1 363 39383 PVEFW-DropBroadcast all -- * * 0.0.0.0/0 0.0.0.0/0
2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 3 code 4
3 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 11
4 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
5 0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 135,445
6 0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpts:137:139
7 0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:137 dpts:1024:65535
8 12 624 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 135,139,445
9 0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:1900
10 52 6554 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:!0x17/0x02
11 0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:53
12 239 13185 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:83WlR/a4wLbmURFqMQT3uJSgIG8 */
Chain PVEFW-DropBroadcast (2 references)
num pkts bytes target prot opt in out source destination
1 60 19020 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type BROADCAST
2 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type MULTICAST
3 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type ANYCAST
4 0 0 DROP all -- * * 0.0.0.0/0 224.0.0.0/4
5 303 20363 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:NyjHNAtFbkH7WGLamPpdVnxHy4w */
Chain PVEFW-FORWARD (1 references)
num pkts bytes target prot opt in out source destination
1 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
2 126K 111M ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
3 9133 634K PVEFW-FWBR-IN all -- * * 0.0.0.0/0 0.0.0.0/0 PHYSDEV match --physdev-in fwln+ --physdev-is-bridged
4 10055 703K PVEFW-FWBR-OUT all -- * * 0.0.0.0/0 0.0.0.0/0 PHYSDEV match --physdev-out fwln+ --physdev-is-bridged
5 28910 2011K all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:qnNexOcGa+y+jebd4dAUqFSp5nw */
Chain PVEFW-FWBR-IN (1 references)
num pkts bytes target prot opt in out source destination
1 9133 634K PVEFW-smurfs all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID,NEW
2 9133 634K all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:Ijl7/xz0DD7LF91MlLCz0ybZBE0 */
Chain PVEFW-FWBR-OUT (1 references)
num pkts bytes target prot opt in out source destination
1 10055 703K all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:2jmj7l5rSw0yVb/vlWAYkK/YBwk */
Chain PVEFW-HOST-IN (1 references)
num pkts bytes target prot opt in out source destination
1 560 143K ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
2 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
3 1070 394K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
4 13 676 PVEFW-smurfs all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID,NEW
5 0 0 RETURN 2 -- * * 0.0.0.0/0 0.0.0.0/0
6 0 0 RETURN icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 8
7 13 676 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 match-set PVEFW-0-ip_admin-v4 src tcp dpt:8006
8 0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 match-set PVEFW-0-ip_admin-v4 src tcp dpt:22
9 0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 match-set PVEFW-0-management-v4 src tcp dpt:8006
10 0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 match-set PVEFW-0-management-v4 src tcp dpts:5900:5999
11 0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 match-set PVEFW-0-management-v4 src tcp dpt:3128
12 0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 match-set PVEFW-0-management-v4 src tcp dpt:22
13 0 0 RETURN tcp -- * * 0.0.0.0/0 0.0.0.0/0 match-set PVEFW-0-management-v4 src tcp dpts:60000:60050
14 0 0 PVEFW-Drop all -- * * 0.0.0.0/0 0.0.0.0/0
15 0 0 NFLOG all -- * * 0.0.0.0/0 0.0.0.0/0 limit: avg 1/sec burst 5 nflog-prefix ":0:7:PVEFW-HOST-IN: policy DROP: "
16 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
17 0 0 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:d57CethE1LtOCvOThQuWHC53G+E */
Chain PVEFW-HOST-OUT (1 references)
num pkts bytes target prot opt in out source destination
1 560 143K ACCEPT all -- * lo 0.0.0.0/0 0.0.0.0/0
2 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
3 975 481K ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
4 0 0 RETURN 2 -- * * 0.0.0.0/0 0.0.0.0/0
5 0 0 NFLOG all -- * * IP_WAN_OPNSENSE 0.0.0.0/0 limit: avg 1/sec burst 5 nflog-prefix ":0:7:PVEFW-HOST-OUT: ACCEPT: "
6 0 0 RETURN all -- * * IP_WAN_OPNSENSE 0.0.0.0/0
7 0 0 NFLOG all -- * * IP_WAN_OPNSENSE 0.0.0.0/0 limit: avg 1/sec burst 5 nflog-prefix ":0:7:PVEFW-HOST-OUT: ACCEPT: "
8 0 0 RETURN all -- * * IP_WAN_OPNSENSE 0.0.0.0/0
9 0 0 RETURN tcp -- * * 0.0.0.0/0 Network_PUB/24 tcp dpt:8006
10 0 0 RETURN tcp -- * * 0.0.0.0/0 Network_PUB/24 tcp dpt:22
11 0 0 RETURN tcp -- * * 0.0.0.0/0 Network_PUB/24 tcp dpts:5900:5999
12 0 0 RETURN tcp -- * * 0.0.0.0/0 Network_PUB/24 tcp dpt:3128
13 94 6124 RETURN all -- * * 0.0.0.0/0 0.0.0.0/0
14 0 0 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:ooiWi8Wr0WriK4zTdqaDNel7O1g */
Chain PVEFW-INPUT (1 references)
num pkts bytes target prot opt in out source destination
1 1643 538K PVEFW-HOST-IN all -- * * 0.0.0.0/0 0.0.0.0/0
2 13 676 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:+5iMmLaxKXynOB/+5xibfx7WhFk */
Chain PVEFW-OUTPUT (1 references)
num pkts bytes target prot opt in out source destination
1 1629 631K PVEFW-HOST-OUT all -- * * 0.0.0.0/0 0.0.0.0/0
2 94 6124 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:LjHoZeSSiWAG3+2ZAyL/xuEehd0 */
Chain PVEFW-Reject (0 references)
num pkts bytes target prot opt in out source destination
1 0 0 PVEFW-DropBroadcast all -- * * 0.0.0.0/0 0.0.0.0/0
2 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 3 code 4
3 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 icmptype 11
4 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
5 0 0 PVEFW-reject udp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 135,445
6 0 0 PVEFW-reject udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpts:137:139
7 0 0 PVEFW-reject udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:137 dpts:1024:65535
8 0 0 PVEFW-reject tcp -- * * 0.0.0.0/0 0.0.0.0/0 multiport dports 135,139,445
9 0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp dpt:1900
10 0 0 DROP tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp flags:!0x17/0x02
11 0 0 DROP udp -- * * 0.0.0.0/0 0.0.0.0/0 udp spt:53
12 0 0 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:h3DyALVslgH5hutETfixGP08w7c */
Chain PVEFW-SET-ACCEPT-MARK (0 references)
num pkts bytes target prot opt in out source destination
1 0 0 MARK all -- * * 0.0.0.0/0 0.0.0.0/0 MARK or 0x80000000
2 0 0 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:Hg/OIgIwJChBUcWU8Xnjhdd2jUY */
Chain PVEFW-logflags (5 references)
num pkts bytes target prot opt in out source destination
1 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
2 0 0 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:MN4PH1oPZeABMuWr64RrygPfW7A */
Chain PVEFW-reject (4 references)
num pkts bytes target prot opt in out source destination
1 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ADDRTYPE match dst-type BROADCAST
2 0 0 DROP all -- * * 224.0.0.0/4 0.0.0.0/0
3 0 0 DROP icmp -- * * 0.0.0.0/0 0.0.0.0/0
4 0 0 REJECT tcp -- * * 0.0.0.0/0 0.0.0.0/0 reject-with tcp-reset
5 0 0 REJECT udp -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-port-unreachable
6 0 0 REJECT icmp -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-unreachable
7 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
8 0 0 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:Jlkrtle1mDdtxDeI9QaDSL++Npc */
Chain PVEFW-smurflog (2 references)
num pkts bytes target prot opt in out source destination
1 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0
2 0 0 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:2gfT1VMkfr0JL6OccRXTGXo+1qk */
Chain PVEFW-smurfs (2 references)
num pkts bytes target prot opt in out source destination
1 100 31700 RETURN all -- * * 0.0.0.0 0.0.0.0/0
2 0 0 PVEFW-smurflog all -- * * 0.0.0.0/0 0.0.0.0/0 [goto] ADDRTYPE match src-type BROADCAST
3 0 0 PVEFW-smurflog all -- * * 224.0.0.0/4 0.0.0.0/0 [goto]
4 9774 657K all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:HssVe5QCBXd5mc9kC88749+7fag */
Chain PVEFW-tcpflags (0 references)
num pkts bytes target prot opt in out source destination
1 0 0 PVEFW-logflags tcp -- * * 0.0.0.0/0 0.0.0.0/0 [goto] tcp flags:0x3F/0x29
2 0 0 PVEFW-logflags tcp -- * * 0.0.0.0/0 0.0.0.0/0 [goto] tcp flags:0x3F/0x00
3 0 0 PVEFW-logflags tcp -- * * 0.0.0.0/0 0.0.0.0/0 [goto] tcp flags:0x06/0x06
4 0 0 PVEFW-logflags tcp -- * * 0.0.0.0/0 0.0.0.0/0 [goto] tcp flags:0x03/0x03
5 0 0 PVEFW-logflags tcp -- * * 0.0.0.0/0 0.0.0.0/0 [goto] tcp spt:0 flags:0x17/0x02
6 0 0 all -- * * 0.0.0.0/0 0.0.0.0/0 /* PVESIG:CMFojwNPqllyqD67NeI5m+bP5mo */