I am doing a fresh install of my Proxmox with VE 8.2.2. because I wanted the OS installed on a ZFS raid 1 filesystem on two NVME ssd drives.
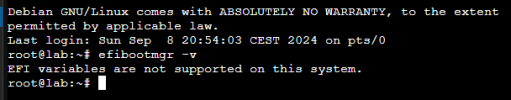
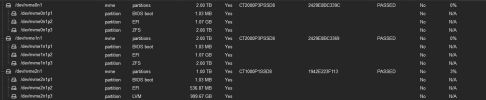
After my install I see my Boot mode = Legacy Bios although I recall that my previous install (not ZFS raid 1 and only one NVME ssd) had Boot mode set to UEFI.
I don't recall an option during the install to choose between the two. UEFI is enabled in BIOS. What did I overlooked?
Macamba
After my install I see my Boot mode = Legacy Bios although I recall that my previous install (not ZFS raid 1 and only one NVME ssd) had Boot mode set to UEFI.
I don't recall an option during the install to choose between the two. UEFI is enabled in BIOS. What did I overlooked?
Macamba