Because the server has only one external IP, I'm using internal NAT.
The problem is, that I can't ping (reach) domains on my VMs and CTs, but I can ping (reach) digit IPs.
Here's some screenshots:


Here is my interfaces configuration:
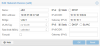
Any help would be welcome
The problem is, that I can't ping (reach) domains on my VMs and CTs, but I can ping (reach) digit IPs.
Here's some screenshots:

Here is my interfaces configuration:
Code:
source /etc/network/interfaces.d/*
auto lo
iface lo inet loopback
auto eno1
iface eno1 inet static
address xxx.xxx.xxx.xxx
netmask xxx.xxx.xxx.xxx
gateway xxx.xxx.xxx.xxx
#External
iface eno2 inet manual
iface eno3 inet manual
iface eno4 inet manual
auto vmbr1
iface vmbr1 inet static
address 10.10.10.1
netmask 255.255.255.0
bridge-ports none
bridge-stp off
bridge-fd 0
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A POSTROUTING -s '10.10.10.0/24' -o eno1 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '10.10.10.0/24' -o eno1 -j MASQUERADE
Any help would be welcome

