Hi Everyone,
I trying build an interfaces file for the following.
I am installing PFsense as a guest on Proxmox. I want it to act as my router, DHCP and firewall. Both for my guest VMs and physical devices (i.e. MacBook) on my switch.
Network Map below. I understand I would need to use VLANs and have tried a number of Interfaces and VLAN setups. But they fail.
Can anyone shed some light on the appropriate proxmox etc/network/interfaces setup?
Let me know if any further information would help
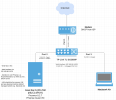
I have tried in terms of /etc/network/interfaces is below:
Config 1
For Config 1 I can access both IPs from my macbook if its directly plugged into proxmox. But not via the switch. If I connect to my switch port 3 with Macbook and Proxmox on Port 2, I get no access or ping response. Also I wonder if PFsense will route properly out to my LAN in this setup:
Config 1 Interfaces File
Config 2
I still have my macbook connected to proxmox directly I can't access 192.168.86.2 or ping. Same via the switch.
Switch Settings as follows:
VLAN ID 1,
Members 1/0/4-8
Ports 4-8 untagged
VLAN ID 10,
Members 1/0/1-2,
Port 1 (WAN) untagged
Port 2 (Proxmox) tagged
VLAN ID 20,
Members 1/0/2-8
Port 2 (Proxmox) tagged
Port 3-8 untagged
I trying build an interfaces file for the following.
I am installing PFsense as a guest on Proxmox. I want it to act as my router, DHCP and firewall. Both for my guest VMs and physical devices (i.e. MacBook) on my switch.
Network Map below. I understand I would need to use VLANs and have tried a number of Interfaces and VLAN setups. But they fail.
Can anyone shed some light on the appropriate proxmox etc/network/interfaces setup?
Let me know if any further information would help

I have tried in terms of /etc/network/interfaces is below:
Config 1
For Config 1 I can access both IPs from my macbook if its directly plugged into proxmox. But not via the switch. If I connect to my switch port 3 with Macbook and Proxmox on Port 2, I get no access or ping response. Also I wonder if PFsense will route properly out to my LAN in this setup:
Config 1 Interfaces File
auto lo
iface lo inet loopback
iface eno1 inet manual
auto vmbr0
iface vmbr0 inet static
address 192.168.86.11/28
gateway 192.168.1.1
bridge-ports eno1
bridge-stp off
bridge-fd 0
bridge-vlan-aware yes
bridge-vids 2-4094
auto vmbr0.10
iface vmbr0.10 inet manual
auto vmbr0.20
iface vmbr0.20 inet static
address 192.168.86.2/28
Config 2
I still have my macbook connected to proxmox directly I can't access 192.168.86.2 or ping. Same via the switch.
auto lo
iface lo inet loopback
iface eno1 inet manual
auto vmbr0
iface vmbr0 inet manual
bridge_ports eno1
bridge_stp off
bridge_fd 0
bridge_vlan_aware yes
bridge-vids 2-4094
auto vmbr0.10
iface vmbr0.10 inet manual
auto vmbr0.20
iface vmbr0.20 inet static
address 192.168.86.2/28
Switch Settings as follows:
VLAN ID 1,
Members 1/0/4-8
Ports 4-8 untagged
VLAN ID 10,
Members 1/0/1-2,
Port 1 (WAN) untagged
Port 2 (Proxmox) tagged
VLAN ID 20,
Members 1/0/2-8
Port 2 (Proxmox) tagged
Port 3-8 untagged
Last edited:

