[SOLVED] I was wondering if i can update the kernel parameters of lxc guest OS?
- Thread starter cqh
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Containers share the same kernel with each other and the Proxmox host. You cannot change kernel parameters from within a container by design. You can change the kernel parameters of the Proxmox host, which (after a reboot) will probably be visible inside the container.
most sysctl parameters should be directly visible after the change. The only one I know which may require a reboot is hugepages, if you do not have any consecutive memory laying around.
Thank you again for your advice.Containers share the same kernel with each other and the Proxmox host. You cannot change kernel parameters from within a container by design. You can change the kernel parameters of the Proxmox host, which (after a reboot) will probably be visible inside the container.
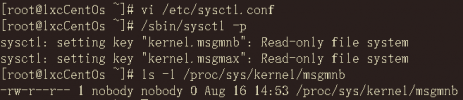
In fact, I have tried it as you said.Things I've done thus far:
- change the kernel parameters of the Proxmox host,and it output:
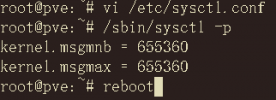
- And then I reboot the host.
- It seems that the kernel parameters in the container have not changed.
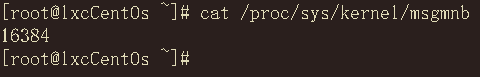
Thank you again for your advice.
I think you need to change the AppArmor restrictions or set capabilities on the LX(C) container in order to get it to work. I have no idea how to loosen the security of the container in order to get it to work. Maybe a real VM would be better here and easier to setup?
Thanks for your reply.I think you need to change the AppArmor restrictions or set capabilities on the LX(C) container in order to get it to work. I have no idea how to loosen the security of the container in order to get it to work. Maybe a real VM would be better here and easier to setup?
I have no idea to loosen the security of the container too
I agree that Containers share the same kernel with the Proxmox host. But it did not work while I changed the kernel parameters.Maybe I overlooked something that caused it not to work properly.
Thank you again.
You cannot change the virtualized parameter you see inside of your container. I debugged it and setting it to unconfined does also not work. You need to create a new apparmor profile in order to get it to work. I would stop here and switch to KVM ... I would not mess around with default security settings so deep.I agree that Containers share the same kernel with the Proxmox host. But it did not work while I changed the kernel parameters.Maybe I overlooked something that caused it not to work properly.
Why do you need to change the setting in the first place?
I installed Proxmox on my home box with the N5105 CPU. It got some problems about crashing VMs.Like the example here: https://forum.proxmox.com/threads/vm-freezes-irregularly.111494/You cannot change the virtualized parameter you see inside of your container. I debugged it and setting it to unconfined does also not work. You need to create a new apparmor profile in order to get it to work. I would stop here and switch to KVM ... I would not mess around with default security settings so deep.
Why do you need to change the setting in the first place?
I switched to Lxc and it work well.
I have an application that must use the message queue of Linux,and found no way to change the kernel parameters from within a container.
could you give a example to create a new apparmor profile please?
Thank you again.
I have never created one until now, but I cannot get it to work:could you give a example to create a new apparmor profile please?
Code:
root@proxmox ~ > cat /etc/apparmor.d/lxc/lxc-default-113710
profile lxc-container-113710 flags=(attach_disconnected,mediate_deleted) {
#include <abstractions/lxc/container-base>
allow /proc/sys/kernel/msg*/** ra,
allow /proc/sys/kernel/msg* ra,
}Reloading:
Code:
apparmor_parser -r /etc/apparmor.d/lxc-containersAdding profile:
Code:
root@proxmox ~ > tail -1 /etc/pve/lxc/100.conf
lxc.apparmor.profile: lxc-container-113710And trying:
Code:
root@proxmox ~ > pct start 100
explicitly configured lxc.apparmor.profile overrides the following settings: features:nesting
root@proxmox ~ > pct exec 100 -- sysctl -w kernel.msgmnb=32768
sysctl: error setting key 'kernel.msgmnb': Read-only file systemYet still no luck. Maybe you can get it to work from here.
I have tried two scenarios of privileged container and non privileged container by modifying AppArmor profile, but it is still no luck so far.I have never created one until now, but I cannot get it to work:
Code:root@proxmox ~ > cat /etc/apparmor.d/lxc/lxc-default-113710 profile lxc-container-113710 flags=(attach_disconnected,mediate_deleted) { #include <abstractions/lxc/container-base> allow /proc/sys/kernel/msg*/** ra, allow /proc/sys/kernel/msg* ra, }
Reloading:
Code:apparmor_parser -r /etc/apparmor.d/lxc-containers
Adding profile:
Code:root@proxmox ~ > tail -1 /etc/pve/lxc/100.conf lxc.apparmor.profile: lxc-container-113710
And trying:
Code:root@proxmox ~ > pct start 100 explicitly configured lxc.apparmor.profile overrides the following settings: features:nesting root@proxmox ~ > pct exec 100 -- sysctl -w kernel.msgmnb=32768 sysctl: error setting key 'kernel.msgmnb': Read-only file system
Yet still no luck. Maybe you can get it to work from here.
Maybe I should read the Proxmox manual carefully.
Anyway, thank you for your help.