Well "switches that support tagged VLANs" thats what managed switches are.. unmanaged switches have no configuration options.
Wrong. "Modern" unmanaged switches have an "automatic learning feature" that allows them to process VLAN tags correctly, even though they don't have any configuration options. But as already said, managed switches make life easier.
He can filter all vlan traffic on his nic using the proxmox firewall so it does not leave the host. I agree with you that if he wants to do serious networking he should get a managed switch, but to isolate some vm's on proxmox its not necessary.
Why should he use the Proxmox firewall? Perhaps he wants to use his "own firewall" (it doesn't matter if hardware or virtual).
He can just use the vm firewall as gateway and setup a static route to access the vlans.
He can use this VM (or an existing hardware) firewall to restrict access between both networks too instead of the Proxmox firewall...
Also proxmox offers splice, vnc etc. which do work well including file transfer, clipboard sharing etc.
Perhaps he want to test systems that offer web or file services like Emby Media Server of FreeNAS or OMV or ...
In this case, SPICE or VNC would be quite useless...
My point was that its easier to do on the firewall appliance, just check a checkbox and youre done.
Nope ... You have to configure VLAN interfaces on the firewall in order to use VLANs too.
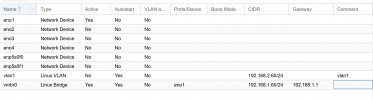
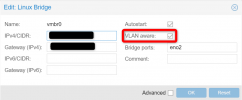
Running a Linux bridge in "VLAN aware mode" is quite easy: check a checkbox ...
... assigne VLAN-IDs to the network interfaces of the VM ...
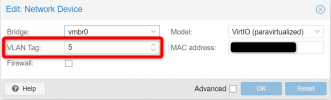
and you're done with VLAN configuration on Proxmox ...
That's an example for a firewall using VLAN aware bridges:

I don't think this is more complicated than configuring VLAN interfaces on a firewall ...

If he just uses vlan aware bridges he wont have internet, he will have to setup outbound nat, routes etc. on its own..
Wrong. As I said before, VLANs and routing, NAT and other protocols belong to different OSI layers, so it doesn't matter if he uses VLAN aware bridges or VLAN interfaces on a firewall, as routing has to be configured anyway, in order to allow internet access for the home and test networks.
Typically, firewalls automatically add routes to directly connected networks. So if you use a firewall as a gateway, both networks will have internet access and it doesn't matter how the VLANs were configured.
Outbound NAT may be necesary or not, depending on the used infrastruture. In example, if his internet router offers the possiblity to add routes, then no outbound NAT is required on the firewall ...
Manually configure that stuff on linux shell for a beginner ?!
Once again, running a linux bridge in "VLAN aware mode" doesn't require manual configuration on the linux shell. It can be done using the Proxmox GUI, as I've shown before.
True for a isolated lan that has no internet just go with bridges, but he stated he wants internet access and that involves more.
There is no relation between "bridges" (layer 2) and internet access (routing, layer 3). A Linux bridge allows VMs to connect to a physical network interface. If the interface is connected to a network with direct internet access, then the VMs will have internet access too. If not, then a gateway (router or firewall) is required. But this fact doesn't depend on using a "bridge" or not...
What issues for example ?
Perhaps VLANs not working correctly, depending on the virtualized firewall?
How is it easier ? Not only you have to do configuration in 2 guis as you also have to set up the interfaces within the firewall. It also adds unnecessary virtualization overhead, just go with 1 interface if you can...
I've shown it before. And you have to configure the firewall interfaces that you need in any case, it doesn't matter if they are network interfaces or subinterfaces (VLANs). But using VLAN aware bridges, you don't need to set up any VLANs on the firewall itself ...
And why should I "go with only one interface", if I can easily add more virtual (native) network interfaces instead of adding VLANs on one virtual (native) interface within the firewall? What is the impact on the performance of the virtualization environment when adding several network interfaces to a VM in comparison to using only one network interface?
This is getting offtopic, its not helping op, setting up a isolated network seems easy but it is not for a beginner.
I don't think that this is getting offtopic at all, as we both are giving enought information and different points of view. And it isn't relevant, which approach is "better". The only relevant thing is the fact, that he can choose which way suits better for him in order to resolve his problem, based on the information that we have given to him. And he may be a beginner, but none of us had the knowhow just from the start, so who cares? It seems to me that he exactly wants to do that: to build up his own knowhow and to learn ...