I've succesfully installed my SSL certificates from StartCom following http://pve.proxmox.com/wiki/HTTPSCertificateConfiguration everything works flawlessly and I'm very happy 
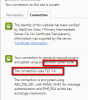
However testing with https://www.digicert.com/help/ tells me that:
Protocol Supported: TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0
SSL 3.0 is an outdated protocol version with known vulnerabilities.
So I've disabled it succesfully everywhere, Apache, NGINX etc. however I don't find a config file to disable SSL v3 for proxmox when connecting directly to port 8006 (it's correctly disabled on NGINX reverse proxy on port 443).
Where can I disable SSL 3.0 altogether in proxmox?
Thank you.
Mic
However testing with https://www.digicert.com/help/ tells me that:
Protocol Supported: TLS 1.2, TLS 1.1, TLS 1.0, SSL 3.0
SSL 3.0 is an outdated protocol version with known vulnerabilities.
So I've disabled it succesfully everywhere, Apache, NGINX etc. however I don't find a config file to disable SSL v3 for proxmox when connecting directly to port 8006 (it's correctly disabled on NGINX reverse proxy on port 443).
Where can I disable SSL 3.0 altogether in proxmox?
Thank you.
Mic