So I am struggling to make this optimal it seems like every way I try to configure this it just does not work the way I want it. I don't want to configure yet another mail gateway just for this it's too painful to manage just one pmg. I understand there are limitations with pmg https://forum.proxmox.com/threads/h...vd-bytecode-cvd-databases.117813/#post-510260 but this for me is a deal breaker and I am considering just finishing my work with pmg and letting someone else deal with it. It's taking too much of my time away from other important work.
My goal for our setup is to have two different configurations (for domains we filter mail):
As far as I understand the highest priority rules will be processed first as I noticed by making whitelist highest priority then viruses were delivered as well if that network/ip was on the whitelist (that is a bad thing).
Action Object Accept, Block, Quarantine are final so if a message is processed with this rule then the message is delivered or blocked or quarantined without any other rules processing.
So how would you set up the priority for all my requirements so they will work the most optimal way they can with proxmox mail gateway?
Here is something I come up with but it does not seem to work the way I want it (main thing right now it's adding disclaimer to blocked messages why it's doing that?? rule OverLevel6BlockSpam is pocessed)
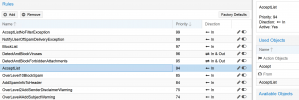
Here are my rules:
1. Blocklist on top because if it's on blocklist it should be blocked no point in processing just block immediately
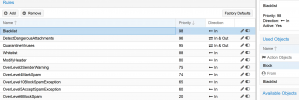
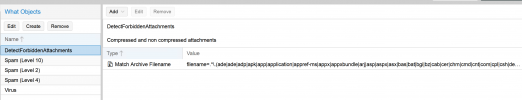
2. If it's a forbidden attachment then it should also block immediately no need to processes any further
3. If there is a virus it should then also block and no need to process any more as we don't want this delivered
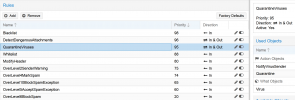
4. This seems like a good place to put whitelist and avoid viruses delivered or other items we don't want to deliver even if they are on whitelist
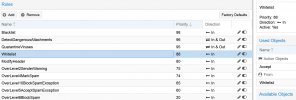
5. This seems like a good place to put modify header spam level so we can see on mails that are delivered what spam score is in the headers. Maybe I should put this before Whitelist that might be even better
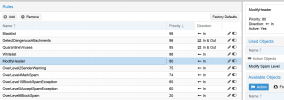
6. spam score 2 add disclaimer to message how will this work? will I have disclaimer on blocked message will this increase processing time?
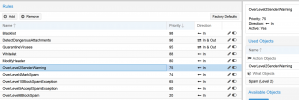
7. spam score 4 modify field: subject on message how will this work? will I have disclaimer on blocked message will this increase processing time?
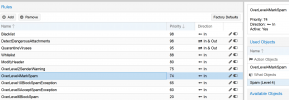
8. don't know if this is correct for my secondary configuration that is more relaxed
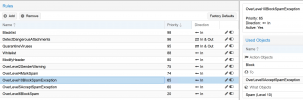
9. don't know if this is correct for my secondary configuration that is more relaxed
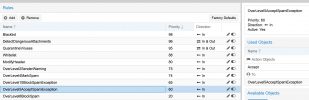
10. final rule again don't know if this is correct
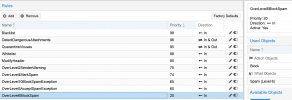
Let me know if you have any idea if this can be improved or should I just give up on two different block levers for domains and just let everything be blocked only if spam score is higher then 10?.
I spend a lot of my brain energy on this and I am stuck how I can improve it so it will work the way I want it to work...
My goal for our setup is to have two different configurations (for domains we filter mail):
- primary configuration that is more aggressive and will block message at spam level 6 (this is the default for almost all domains)
- secondary configuration that is more relaxed and will block at spam level 10 (for some domains the default setup is too aggressive) rule OverLevel5AcceptSpamException
- processing should be minimized if possible (no adding of disclaimer or modify field: subject if message is to be blocked) ?
- every message spam level higher then 2 add disclaimer to message (OverLevel2SenderWarning rule)
- every message spam level higher then 4 modify field: subject (OverLevel4MarkSpam rule)
- every message that contains virus block and notify sender (?)
- every message that contains forbidden attachment block and notify sender (?)
- whitelist and blocklist should work also for both configurations (?)
- how to minimize processing I see that in my current configuration disclaimer is added on messages that are blocked
- should I actually notify sender if they are sending a virus message (some mail providers will not notify sender if message is detected as virus by pmg (example google mail) right now I see that someone is sending virus from some compromised server and in the envelope from another domain so we are sending notifications to sender that is not actually sending virus that is bad like really bad it should not do that
- I want to make sure if someone is sending messages that contain forbidden attachment they are notified that they are sending forbidden attachment (but want to minimize the notifications for spam senders that will send massive amounts of messages with forbidden attachment)
- I want the detected message virus or forbidden attachment in the quarantine for analytics so if I need to report a false positive I can and I have the data this is not possible if I want to use block rule and I want to have message in the quarantine
- where to actually put whitelist or blocklist priority. I don't want virus delivery even if domain/network,ip ect is on whitelist
As far as I understand the highest priority rules will be processed first as I noticed by making whitelist highest priority then viruses were delivered as well if that network/ip was on the whitelist (that is a bad thing).
Action Object Accept, Block, Quarantine are final so if a message is processed with this rule then the message is delivered or blocked or quarantined without any other rules processing.
So how would you set up the priority for all my requirements so they will work the most optimal way they can with proxmox mail gateway?
Here is something I come up with but it does not seem to work the way I want it (main thing right now it's adding disclaimer to blocked messages why it's doing that?? rule OverLevel6BlockSpam is pocessed)
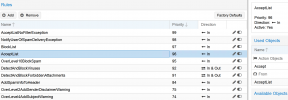
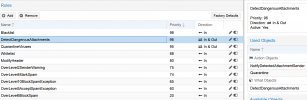
Here are my rules:
1. Blocklist on top because if it's on blocklist it should be blocked no point in processing just block immediately

2. If it's a forbidden attachment then it should also block immediately no need to processes any further

3. If there is a virus it should then also block and no need to process any more as we don't want this delivered

4. This seems like a good place to put whitelist and avoid viruses delivered or other items we don't want to deliver even if they are on whitelist

5. This seems like a good place to put modify header spam level so we can see on mails that are delivered what spam score is in the headers. Maybe I should put this before Whitelist that might be even better

6. spam score 2 add disclaimer to message how will this work? will I have disclaimer on blocked message will this increase processing time?

7. spam score 4 modify field: subject on message how will this work? will I have disclaimer on blocked message will this increase processing time?

8. don't know if this is correct for my secondary configuration that is more relaxed

9. don't know if this is correct for my secondary configuration that is more relaxed

10. final rule again don't know if this is correct

Let me know if you have any idea if this can be improved or should I just give up on two different block levers for domains and just let everything be blocked only if spam score is higher then 10?.
I spend a lot of my brain energy on this and I am stuck how I can improve it so it will work the way I want it to work...