Dear,
I installed adguardhome as my home network dns "server"
I have a homelab with a pve server hosting a couple of vm ( nextcloud, influxdb...)
those vm are backuped to remote PBD instance ( kindly offered by tuxis.nl) and to a local PBS ( lorath-adm.phi8.ovh)
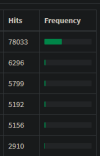
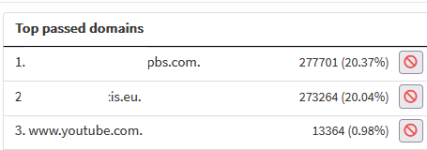
the statistics page of adguardhome show that almos 45% of DNS requests served by adguardhome are for the two PBS hostnames.
Is this normal ?
How/where can I start investigating/diagnosing this issue ?
Thanks in adance
EC
I installed adguardhome as my home network dns "server"
I have a homelab with a pve server hosting a couple of vm ( nextcloud, influxdb...)
those vm are backuped to remote PBD instance ( kindly offered by tuxis.nl) and to a local PBS ( lorath-adm.phi8.ovh)
the statistics page of adguardhome show that almos 45% of DNS requests served by adguardhome are for the two PBS hostnames.
Is this normal ?
How/where can I start investigating/diagnosing this issue ?
Thanks in adance
EC

12:26:18
11/5/2022
monitor.phi8.ovh
Type: AAAA, Plain DNS
Processed
0.56 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.21%22']172.19.1.21[/URL]
12:26:13
11/5/2022
lorath-adm.phi8.ovh
Type: AAAA, Plain DNS
Processed
0.41 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
12:26:13
11/5/2022
lorath-adm.phi8.ovh
Type: A, Plain DNS
Processed
0.12 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
12:26:13
11/5/2022
pbs001.tuxis.nl
Type: AAAA, Plain DNS
Processed
0.21 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
12:26:13
11/5/2022
pbs001.tuxis.nl
Type: A, Plain DNS
Processed
0.17 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
12:26:13
11/5/2022
pbs001.tuxis.nl
Type: AAAA, Plain DNS
Processed
0.08 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
12:26:13
11/5/2022
pbs001.tuxis.nl
Type: A, Plain DNS
Processed
0.12 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
12:26:08
11/5/2022
monitor.phi8.ovh
Type: AAAA, Plain DNS
Processed
0.44 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.21%22']172.19.1.21[/URL]
12:26:05
11/5/2022
pbs001.tuxis.nl
Type: A, Plain DNS
Processed
0.08 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
12:26:05
11/5/2022
pbs001.tuxis.nl
Type: AAAA, Plain DNS
Processed
0.16 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
12:26:05
11/5/2022
pbs001.tuxis.nl
Type: AAAA, Plain DNS
Processed
0.08 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]
Block
12:26:05
11/5/2022
pbs001.tuxis.nl
Type: A, Plain DNS
Processed
0.13 ms
[URL='http://thewall.phi8.ovh:3080/#logs?search=%22172.19.1.100%22']172.19.1.100[/URL]