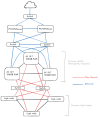
I need an infrastructure to create and provide vms / containers and virtualized infrastructures (Active Directories etc)
I've little knowledge about IT infrastructure and spent days researching stuff that lead me to create this diagram.
Am I on the right path for the general idea, is it feasible or do you see a glaring mistake ?
Thanks!
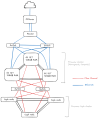
I've little knowledge about IT infrastructure and spent days researching stuff that lead me to create this diagram.
Am I on the right path for the general idea, is it feasible or do you see a glaring mistake ?
Thanks!

Last edited: