I want to share my frustration with PMG, it seems that nothing is really working as described.
The purpose of the gui is to simplify usability and if there is a rule be it who or what, and you add the rule according to the documentation it should work.
Yes, there may be occasions where something doesn't, however you can't have 30 rules, and none work.
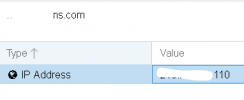
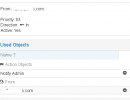
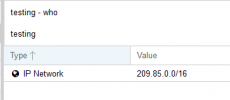
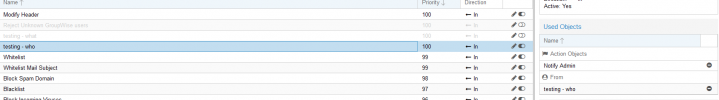
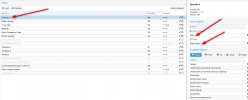
As an example I read through the documentation and it says to block IP's, add it in WHO, so you go to who->blacklist-> IP or IP Network.
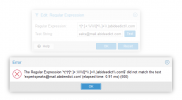
Adding a rule there doesn't work.
Sharing the information in a post, I really don't get an answer to simply make it work.
So I search some more posts and find the below 2.
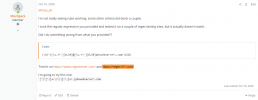
In this post we're told add it to the who
https://forum.proxmox.com/threads/blacklist-ip-address.352/
In this post it says it wont work
https://forum.proxmox.com/threads/ip-network-blacklists.71362/
So if this doesn't work, why don't we either change the code to block the IP's in the proper way as described in the 2nd post,
or remove the feature from the GUI since it doesn't work giving the user a false sense of security.
First, I have to thank everyone on the forum that tries to help, but there has to be more of an example and working answers.
If you can't block something as mentioned in the above 2nd post, then say it, not to create some random other rule to try and block the information which doesn't work.
That was the purpose of adding the who->blacklist->ip.
To share, yes I am a subscriber, not at a high level but wanted to help the project as I try out this tool.
2nd I have run postfix servers for several years manually, which works well, but doesn't make it easy for people with less knowledge to manage, so PMG sounds like it fills a void.
I appreciate all the contributors at the code level, forum etc.
I simply want to use the tool as described and have it work and not spend countless hours and frustration trying to get it to work, to find out it won't.
The purpose of the gui is to simplify usability and if there is a rule be it who or what, and you add the rule according to the documentation it should work.
Yes, there may be occasions where something doesn't, however you can't have 30 rules, and none work.
As an example I read through the documentation and it says to block IP's, add it in WHO, so you go to who->blacklist-> IP or IP Network.
Adding a rule there doesn't work.
Sharing the information in a post, I really don't get an answer to simply make it work.
So I search some more posts and find the below 2.
In this post we're told add it to the who
https://forum.proxmox.com/threads/blacklist-ip-address.352/
In this post it says it wont work
https://forum.proxmox.com/threads/ip-network-blacklists.71362/
So if this doesn't work, why don't we either change the code to block the IP's in the proper way as described in the 2nd post,
or remove the feature from the GUI since it doesn't work giving the user a false sense of security.
First, I have to thank everyone on the forum that tries to help, but there has to be more of an example and working answers.
If you can't block something as mentioned in the above 2nd post, then say it, not to create some random other rule to try and block the information which doesn't work.
That was the purpose of adding the who->blacklist->ip.
To share, yes I am a subscriber, not at a high level but wanted to help the project as I try out this tool.
2nd I have run postfix servers for several years manually, which works well, but doesn't make it easy for people with less knowledge to manage, so PMG sounds like it fills a void.
I appreciate all the contributors at the code level, forum etc.
I simply want to use the tool as described and have it work and not spend countless hours and frustration trying to get it to work, to find out it won't.