Hello, hopefully you can help me with this issue.
My Configuration:
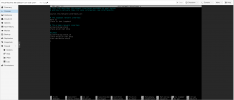
Firewall on Datacenter, Node and VM are turned on. Input Policy = Deny.
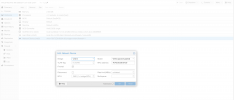
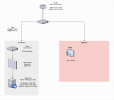
I have a Linux Bridge with the Option "VLANS aware = yes"
On the VM I have configured the Network Device without a VLAN Tag.
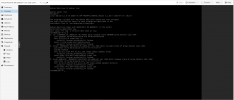
The VM has the IP 10.10.1.2 on eth0.
Additionally I have configured a Interface eth0.10 (VLAN10) inside the VM with the IP 10.10.10.2.
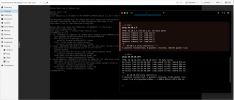
Now I can´t Ping 10.10.1.2 (eth0), but i can ping 10.10.10.2 (eth0.10) from outside.
It´s seems like the Firewall in Proxmox does not effect to VLANs that are assigned in the VM itself.
If I delete the Interface eth0.10 and create a second Network device on the Proxmox GUI with VLAN Tag= 10 than the Firewall blocks the Ping on both interfaces as it should.
Is this a bug or do i miss something?
My Configuration:
Firewall on Datacenter, Node and VM are turned on. Input Policy = Deny.
I have a Linux Bridge with the Option "VLANS aware = yes"
On the VM I have configured the Network Device without a VLAN Tag.
The VM has the IP 10.10.1.2 on eth0.
Additionally I have configured a Interface eth0.10 (VLAN10) inside the VM with the IP 10.10.10.2.
Now I can´t Ping 10.10.1.2 (eth0), but i can ping 10.10.10.2 (eth0.10) from outside.
It´s seems like the Firewall in Proxmox does not effect to VLANs that are assigned in the VM itself.
If I delete the Interface eth0.10 and create a second Network device on the Proxmox GUI with VLAN Tag= 10 than the Firewall blocks the Ping on both interfaces as it should.
Is this a bug or do i miss something?