@jsterr thank you!
This is the output of that command. Do you think that it is whitelisting the whole subnet?
The odd thing is that in explicitly list the security group in the logs so if it is inherently whitelisting the sub, it is giving the reason the security group with its limited definition.
root@pve:~# pve-firewall localnet
local hostname: pve
local IP address: 10.10.20.30
network auto detect: 10.10.20.0/23
using detected local_network: 10.10.20.0/23
accepting corosync traffic from/to:
- pve2: 10.10.20.40 (link: 0)
- pve3: 10.10.20.50 (link: 0)
More info:
root@pve:~# cat /etc/pve/firewall/cluster.fw
[OPTIONS]
enable: 1
policy_in: DROP
[ALIASES]
GNET-4FYH325C 10.10.21.65 # Work Mac
UserPhone 10.10.20.241 # UserPhone
NPM 10.0.30.201 # Nginx Proxy Manager
pve 10.10.20.30 # Proxmox virtual environment
pve2 10.10.20.40 # Proxmox virtual environment 2
pve3 10.10.20.50 # Proxmox virtual environment 3
Unraid-Nova 10.0.30.48 # Backup Server
XPS8940 10.10.21.45 # Office Desktop
[IPSET management] # Authorized Computers
dc/gnet-4fyh325c # Work Mac
dc/userphone # userPhone
dc/npm # Proxy
dc/unraid-nova # Backup Server
dc/xps8940 # Office Desktop
[IPSET pve_hosts] # Proxmox Server IPs
dc/pve
dc/pve2
dc/pve3
[RULES]
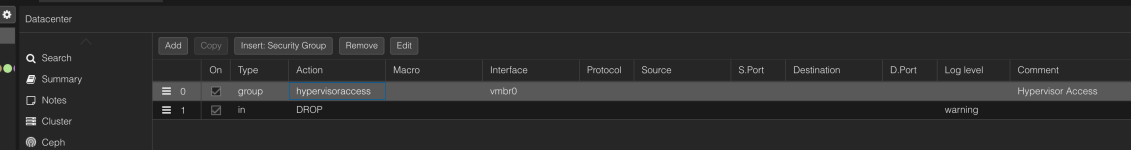
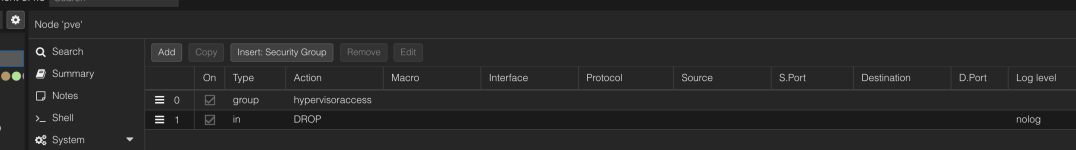
GROUP hypervisoraccess -i vmbr0 # Hypervisor Access
IN DROP -log warning
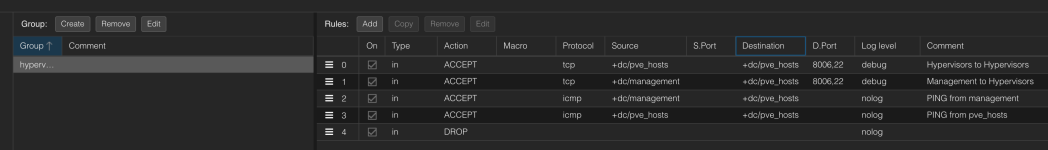
[group hypervisoraccess]
IN ACCEPT -source +dc/pve_hosts -dest +dc/pve_hosts -p tcp -dport 8006,22 -log debug # Hypervisors to Hypervisors
IN ACCEPT -source +dc/management -dest +dc/pve_hosts -p tcp -dport 8006,22 -log debug # Management to Hypervisors
IN ACCEPT -source +dc/management -dest +dc/pve_hosts -p icmp -log nolog -icmp-type any # PING from management
IN ACCEPT -source +dc/pve_hosts -dest +dc/pve_hosts -p icmp -log nolog -icmp-type any # PING from pve_hosts
IN DROP -log nolog