Hi I just wanted to set up firewalls like showcased in many of the youtube videos.
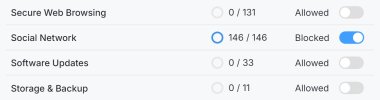
Added the following datacenter rules:
Enabled firewall on datacenter, node and vm.
When experimenting on datacenter level traffic to the nodes can be controlled and for example ssh is currently off, this can be tested and verified.
However I can still ping my vms, lxcs access them via ssh and connect to their webserver -> But I expect the default drop all incoming to disabled this.
Nontheless I created a block all incoming directly on the container:

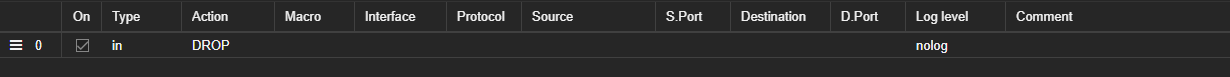
I can still ping and access the vm normally, without any problems.
What do I need to do to get this firewall to block traffic on vm/lxc level??
Added the following datacenter rules:

Enabled firewall on datacenter, node and vm.
When experimenting on datacenter level traffic to the nodes can be controlled and for example ssh is currently off, this can be tested and verified.
However I can still ping my vms, lxcs access them via ssh and connect to their webserver -> But I expect the default drop all incoming to disabled this.
Nontheless I created a block all incoming directly on the container:


I can still ping and access the vm normally, without any problems.
What do I need to do to get this firewall to block traffic on vm/lxc level??