Good Morning,
currently i'm messing around with my local networks. I decided to add a DHCP Server and an option to reverse proxy some parts of my local net (green, blue) to campus (red) access.
I have followed some youtube tutorials (german). Unfortunately, i can't get access to the pfsense over the ip on vmbr1. I do have access to proxmox via ssh and http (8006).
Here i have a diagram of my current approach:
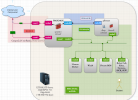
I could have as many ip's i'd need - i could even bring the vm's upfront in the campusnet. My idea is to expose the pfsense vm to campusnet and have the routing and access to apps/vm's from campusnet (red) to robonet (green) and robonet to internet (with proxy and 802.1x)
currently i'm messing around with my local networks. I decided to add a DHCP Server and an option to reverse proxy some parts of my local net (green, blue) to campus (red) access.
I have followed some youtube tutorials (german). Unfortunately, i can't get access to the pfsense over the ip on vmbr1. I do have access to proxmox via ssh and http (8006).
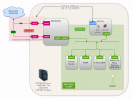
Here i have a diagram of my current approach:

I could have as many ip's i'd need - i could even bring the vm's upfront in the campusnet. My idea is to expose the pfsense vm to campusnet and have the routing and access to apps/vm's from campusnet (red) to robonet (green) and robonet to internet (with proxy and 802.1x)

Bash:
auto lo
iface lo inet loopback
iface eno2 inet manual
auto eno1
iface eno1 inet static
hwaddress ac:1f:6b:e9:6e:56
# zuweisung virtueller FAKE MAC um doppelte dhcp anfrage zu vermeiden
auto vmbr1
iface vmbr1 inet dhcp
hwaddress ac:1f:6b:e9:7e:56
wpa-conf /etc/wpa_supplicant/wpasupp.conf
wpa-driver wired
wpa-logfile /var/log/eit-wpa.log
wpa-debug-level 2
bridge-ports eno1
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up iptables -t nat -A PREROUTING -i vmbr1 -p tcp -m multiport ! --dport 22,8006 -j DNAT --to 192.0.0.2
post-up iptables -t nat -A PREROUTING -i vmbr1 -p udp -j DNAT --to 192.0.0.2
post-up ip route replace default via 10.152.47.254 dev vmbr1
post-down ip route replace default via 10.152.116.254 dev vmbr3
# eit-w1, Zuweisung der originalen NIC ENO1 MAC.
# Öffnen der Firewall für alle ports außer 22 und 8006. April2022: 80 und 443 für nginx baremetal - wurde wieder entfernt für tests (16.8.2022)
# Öffnen aller udp ports zur pfsense
auto enx00e04c680542
iface enx00e04c680542 inet manual
altname eno3
# USB NIC für vmbr3 IRAS-W0
auto vmbr3
iface vmbr3 inet dhcp
hwaddress ac:1f:6b:e9:7e:73
bridge-ports enx00e04c680542
bridge-stp off
bridge-fd 0
# post-up ip route del default via vmbr3
# IRAS W0 Brücke für VM ans ADS - Netzwerk. Funktioniert auch...
auto vmbr2
iface vmbr2 inet static
address 172.31.1.25/16
bridge-ports eno2
bridge-stp off
bridge-fd 0
hwaddress ac:1f:6b:e9:7f:60
# robonet, lokaler Zugriff über eno2. NAT Forwarding kommt dann über die Pfsense
auto vmbr100
iface vmbr100 inet static
address 192.0.0.1/30
bridge-ports none
bridge-stp off
bridge-fd 0
hwaddress ac:1f:6b:e9:7f:61
post-up iptables -t nat -A POSTROUTING -s '192.0.0.0/30' -o vmbr1 -j MASQUERADE
post-down iptables -t nat -D POSTROUTING -s '192.0.0.0/30' -o vmbr1 -j MASQUERADE
# firenet Brücke zur Firewall und nur für Kommunikation von Server zu Firewall mit NAT und PAT
#https://linuxhint.com/debian_network_interface_setup/
#https://wiki.debian.org/NetworkConfiguration#Using_DHCP_to_automatically_configure_the_interface
Bash:
iptables-save
# Generated by iptables-save v1.8.7 on Fri Aug 19 09:58:37 2022
*raw
:PREROUTING ACCEPT [1657405:280642520]
:OUTPUT ACCEPT [889312:135486360]
COMMIT
# Completed on Fri Aug 19 09:58:37 2022
# Generated by iptables-save v1.8.7 on Fri Aug 19 09:58:37 2022
*filter
:INPUT ACCEPT [1019003:211287982]
:FORWARD ACCEPT [110:6600]
:OUTPUT ACCEPT [889331:135489198]
COMMIT
# Completed on Fri Aug 19 09:58:37 2022
# Generated by iptables-save v1.8.7 on Fri Aug 19 09:58:37 2022
*nat
:PREROUTING ACCEPT [347323:32863628]
:INPUT ACCEPT [4501:1025800]
:OUTPUT ACCEPT [64039:4096550]
:POSTROUTING ACCEPT [64058:4097690]
-A PREROUTING -i vmbr1 -p tcp -m multiport ! --dports 22,8006 -j DNAT --to-destination 192.0.0.2
-A PREROUTING -i vmbr1 -p udp -j DNAT --to-destination 192.0.0.2
-A PREROUTING -i vmbr1 -p tcp -m multiport ! --dports 22,8006 -j DNAT --to-destination 192.0.0.2
-A POSTROUTING -s 192.0.0.0/30 -o vmbr1 -j MASQUERADE
COMMIT
# Completed on Fri Aug 19 09:58:37 2022
Bash:
ip r
default via 10.152.47.254 dev vmbr1
10.152.32.0/20 dev vmbr1 proto kernel scope link src 10.152.32.76
10.181.116.0/22 dev vmbr3 proto kernel scope link src 10.181.116.185
172.31.0.0/16 dev vmbr2 proto kernel scope link src 172.31.1.25
192.0.0.0/30 dev vmbr100 proto kernel scope link src 192.0.0.1
Code:
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eno1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master vmbr1 state UP group default qlen 1000
link/ether ac:1f:6b:e9:6e:56 brd ff:ff:ff:ff:ff:ff permaddr ac:1f:6b:e9:7e:56
altname enp196s0
3: eno2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master vmbr2 state UP group default qlen 1000
link/ether ac:1f:6b:e9:7e:57 brd ff:ff:ff:ff:ff:ff
altname enp197s0
4: enx00e04c680542: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast master vmbr3 state UP group default qlen 1000
link/ether 00:e0:4c:68:05:42 brd ff:ff:ff:ff:ff:ff
5: vmbr1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether ac:1f:6b:e9:7e:56 brd ff:ff:ff:ff:ff:ff
inet 10.152.32.76/20 brd 10.152.47.255 scope global dynamic vmbr1
valid_lft 35881sec preferred_lft 35881sec
inet6 fe80::ae1f:6bff:fee9:7e56/64 scope link
valid_lft forever preferred_lft forever
6: vmbr3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether ac:1f:6b:e9:7e:73 brd ff:ff:ff:ff:ff:ff
inet 10.181.116.185/22 brd 10.181.119.255 scope global dynamic vmbr3
valid_lft 30231sec preferred_lft 30231sec
inet6 fe80::ae1f:6bff:fee9:7e73/64 scope link
valid_lft forever preferred_lft forever
7: vmbr2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether ac:1f:6b:e9:7f:60 brd ff:ff:ff:ff:ff:ff
inet 172.31.1.25/16 scope global vmbr2
valid_lft forever preferred_lft forever
inet6 fe80::ae1f:6bff:fee9:7f60/64 scope link
valid_lft forever preferred_lft forever
8: vmbr100: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP group default qlen 1000
link/ether ac:1f:6b:e9:7f:61 brd ff:ff:ff:ff:ff:ff
inet 192.0.0.1/30 scope global vmbr100
valid_lft forever preferred_lft forever
inet6 fe80::ae1f:6bff:fee9:7f61/64 scope link
valid_lft forever preferred_lft forever
valid_lft forever preferred_lft forever
