Hi there,
I've enabled an IPSet "Management" in my Firewall and added some IPs (home office and company).
But my homeoffice sometimes changes the IP. Therefore I've configured all other systems, firewalls etc I need access to, to simply use a Domainname instead of the IP.
Simply said, I'm using a DynDNS service not to connect to my office, but allow my office to connect elsewhere.
I wonder how I could achieve the same with the Proxmox Firewall?
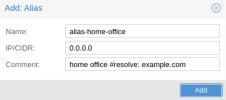
I didn't find an option to add a domain instead of an IP.
Would be glad if someone can point me in the right direction.
Regards,
Michael
I've enabled an IPSet "Management" in my Firewall and added some IPs (home office and company).
But my homeoffice sometimes changes the IP. Therefore I've configured all other systems, firewalls etc I need access to, to simply use a Domainname instead of the IP.
Simply said, I'm using a DynDNS service not to connect to my office, but allow my office to connect elsewhere.
I wonder how I could achieve the same with the Proxmox Firewall?
I didn't find an option to add a domain instead of an IP.
Would be glad if someone can point me in the right direction.
Regards,
Michael