We have had good success with the Secure Boot capable EFI disks and TPM v2.0 emulation. Tested on latest no-subscription with Ceph Pacific 16.2.6. Live migrate works with Windows 11 with full disk encryption (BitLocker) and everything works just perfectly as long as one selects the start/shutdown/migrate options. Issuing a stop instruction results in EFI and TPM references being removed from the VM configuration file.
Nice work, looking forward to this landing in the enterprise repo soon!
Works perfectly when you use 'shutdown' instead of 'stop':
Windows 11 with Secure Boot enabled:
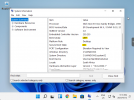
Destroyed the test Windows 11 system where BitLocker was working, unfortunatley didn't take a snippet from it but it worked flawlessly.
Nice work, looking forward to this landing in the enterprise repo soon!
Code:
[admin@kvm1d ~]# cat /etc/pve/nodes/kvm1d/qemu-server/122.conf > /root/122.conf.backup; cat /etc/pve/nodes/kvm1d/qemu-server/122.conf
agent: 1
bios: ovmf
boot: order=scsi0;ide2;net0
cores: 1
cpu: Westmere,flags=+pcid
efidisk0: rbd_hdd:vm-122-disk-1,efitype=4m,pre-enrolled-keys=1,size=1M
ide2: none,media=cdrom
localtime: 1
machine: pc-q35-6.0
memory: 4096
name: lair-temp
net0: virtio=00:16:3e:00:01:12,bridge=vmbr0,tag=1
numa: 1
ostype: win10
protection: 1
scsi0: rbd_hdd:vm-122-disk-0,cache=writeback,discard=on,size=80G,ssd=1
scsihw: virtio-scsi-pci
smbios1: uuid=f45692f6-0e09-48d2-ae74-7ce85f3f3267
sockets: 2
tpmstate0: rbd_hdd:vm-122-disk-2,size=4M,version=v2.0
[admin@kvm1d ~]# rbd showmapped | grep -e namespace -e 122
id pool namespace image snap device
10 rbd_hdd vm-122-disk-1 - /dev/rbd10
[admin@kvm1d ~]# rbd ls rbd_hdd -l | grep -e NAME -e 122
NAME SIZE PARENT FMT PROT LOCK
vm-122-disk-0 80 GiB 2
vm-122-disk-1 1 MiB 2 excl
vm-122-disk-2 4 MiB 2
[admin@kvm1d ~]# qm start 122; sleep 45; qm stop 122; sleep 20;
Requesting HA start for VM 122
Requesting HA stop for VM 122
[admin@kvm1d ~]# rbd showmapped | grep -e namespace -e 122
id pool namespace image snap device
10 rbd_hdd vm-122-disk-1 - /dev/rbd10
[admin@kvm1d ~]# rbd ls rbd_hdd -l | grep -e NAME -e 122
NAME SIZE PARENT FMT PROT LOCK
vm-122-disk-0 80 GiB 2
vm-122-disk-1 1 MiB 2 excl
vm-122-disk-2 4 MiB 2
[admin@kvm1d ~]# diff -uNr /root/122.conf.backup /etc/pve/nodes/kvm1d/qemu-server/122.conf
--- /root/122.conf.backup 2021-10-12 21:52:49.922585883 +0200
+++ /etc/pve/nodes/kvm1d/qemu-server/122.conf 2021-10-12 21:55:49.000000000 +0200
@@ -3,7 +3,6 @@
boot: order=scsi0;ide2;net0
cores: 1
cpu: Westmere,flags=+pcid
-efidisk0: rbd_hdd:vm-122-disk-1,efitype=4m,pre-enrolled-keys=1,size=1M
ide2: none,media=cdrom
localtime: 1
machine: pc-q35-6.0
@@ -17,4 +16,3 @@
scsihw: virtio-scsi-pci
smbios1: uuid=f45692f6-0e09-48d2-ae74-7ce85f3f3267
sockets: 2
-tpmstate0: rbd_hdd:vm-122-disk-2,size=4M,version=v2.0Works perfectly when you use 'shutdown' instead of 'stop':
Code:
[admin@kvm1d ~]# cat /root/122.conf.backup > /etc/pve/nodes/kvm1d/qemu-server/122.conf
[admin@kvm1d ~]# qm start 122; sleep 45; qm shutdown 122; sleep 20;
[admin@kvm1d ~]# kill 1069131
[admin@kvm1d ~]# rbd showmapped | grep -e namespace -e 122;
id pool namespace image snap device
10 rbd_hdd vm-122-disk-1 - /dev/rbd10
11 rbd_hdd vm-122-disk-0 - /dev/rbd11
[admin@kvm1d ~]# rbd ls rbd_hdd -l | grep -e NAME -e 122;
NAME SIZE PARENT FMT PROT LOCK
vm-122-disk-0 80 GiB 2 excl
vm-122-disk-1 1 MiB 2 excl
vm-122-disk-2 4 MiB 2
[admin@kvm1d ~]# diff -uNr /root/122.conf.backup /etc/pve/nodes/kvm1d/qemu-server/122.conf
<blank>Windows 11 with Secure Boot enabled:

Destroyed the test Windows 11 system where BitLocker was working, unfortunatley didn't take a snippet from it but it worked flawlessly.
Last edited:

