I have built my first proxmox home server. I have proxmox installed on 2x 120GB ssd, and I have 2x 1TB sdd as my primary storage for VM and Containers.
When I create a new vm, the vm fails when booted up with the errors shown below. I have tried reinstalling proxmox and redoing the vm, but the same error occurs. I also tried using BTFRS as a last resort but that had its own errors, and I would rather use ZFS anyways. I have tried swapping between 120gb and 1TB as the boot drive for proxmox + local storage drive, but the same error shown on the screenshot occurs.
Motherboard: B550M AORUS PRO-P
CPU: AMD Ryzen 7 5700G
SSD: 2x 120GB Kingston
2x 1TB Crucial
I am new to both proxmox and ZFS, so I may be missing something obvious.
It does seem from the logs that when the VM is initialized that all devices get brought down, usb keyboard, my ethernet connection, etc. I am not passing those devices into the VM. The VM doesnt have any network interfaces as I am doing PCI passthrough of my intel quad gigabit card into the vm.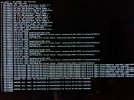
When I create a new vm, the vm fails when booted up with the errors shown below. I have tried reinstalling proxmox and redoing the vm, but the same error occurs. I also tried using BTFRS as a last resort but that had its own errors, and I would rather use ZFS anyways. I have tried swapping between 120gb and 1TB as the boot drive for proxmox + local storage drive, but the same error shown on the screenshot occurs.
Motherboard: B550M AORUS PRO-P
CPU: AMD Ryzen 7 5700G
SSD: 2x 120GB Kingston
2x 1TB Crucial
I am new to both proxmox and ZFS, so I may be missing something obvious.
It does seem from the logs that when the VM is initialized that all devices get brought down, usb keyboard, my ethernet connection, etc. I am not passing those devices into the VM. The VM doesnt have any network interfaces as I am doing PCI passthrough of my intel quad gigabit card into the vm.

Last edited:

