Disable Root Account
- Thread starter Lioh
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Sounds like a lot of overhead to me 
The question is: is the root account a built-in or is it not there by default. If it's a built-in account, is it safe to remove/disable it within the gui (as long as there are other accounts with similar permissions available of course).
Greetings
Lioh
The question is: is the root account a built-in or is it not there by default. If it's a built-in account, is it safe to remove/disable it within the gui (as long as there are other accounts with similar permissions available of course).
Greetings
Lioh
root is the linux
the thing is a lot of options on PVE are permitted for root@pam user only, so disabling it would limit your options quite a bit.
you could remove the root password to achieve the same thing, that way you cannot login as root@pam directly but still be able to
root@pam userthe thing is a lot of options on PVE are permitted for root@pam user only, so disabling it would limit your options quite a bit.
you could remove the root password to achieve the same thing, that way you cannot login as root@pam directly but still be able to
sudo to it from a shell (although i think you'd still be unable to use root@pam on the GUI)For SSH it's not really an issue as we are limiting to key based access. Console login and gui is what it's about. So I am going to try to disable the root pw on Linux and see where the telephone will fall from the table
Where did the phone fall?For SSH it's not really an issue as we are limiting to key based access. Console login and gui is what it's about. So I am going to try to disable the root pw on Linux and see where the telephone will fall from the table
I am wanting to do the same so interested to hear how successful you were.
Graham
Also interested in what @Lioh uncovers, as we have a similar situation at work with users sourced from Active Directory, and most day-to-day operations can be achieved via non-root users. Root via local ssh is always a fallback for any advanced configuration changes or diagnostics.
Seems like if disabling root under Users in the web gui turns out to be a Bad Thing To Do™ then it shouldn't be allowed to be disabled. Just my 2c on user interface (not a designer by any means).
Seems like if disabling root under Users in the web gui turns out to be a Bad Thing To Do™ then it shouldn't be allowed to be disabled. Just my 2c on user interface (not a designer by any means).
Last edited:
Just tried @Lioh idea of deleting root password on CLI, and seems to be working so far! root user still exists in Linux environment, and can be accessed with a privileged user. From GUI, root user fails to login. I'm interested to know if anyone experiences any issues, but so far none for me.
only thing that can be problematic would be calling some root-only API endpoints.I'm interested to know if anyone experiences any issues, but so far none for me.
you can follow this feature request [0], we're working on creating a privilege to enable root-only actions over the API
[0]: https://bugzilla.proxmox.com/show_bug.cgi?id=2582
Hi guys,
I know it's old post, but i can write a little guide book. You need create a new account for manage your PVE and give the permission for administrator. You install sudoers function for give root access, add your new account to the sudoers configuration.
You can disable shell login in : /etc/passwd
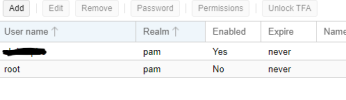
Now you can disable login in pve web admin.
I add two screenshot in below, for see this.
bye
I know it's old post, but i can write a little guide book. You need create a new account for manage your PVE and give the permission for administrator. You install sudoers function for give root access, add your new account to the sudoers configuration.
You can disable shell login in : /etc/passwd
Now you can disable login in pve web admin.
I add two screenshot in below, for see this.
bye
Attachments
Still the problem that some stuff (I think joining cluster and so on) is hardcoded to be only be usable by root. So later you might need to enable root again as another user with administrative privileges isn't a full replacement.
I also see a problem in live migration, which needs to log in into other nodes and therefore be able to login.You can disable shell login in : /etc/passwd
Why don't you just do what @oguz said and disable the password?
Is the permission problem on root-only API endpoints is not fixed yet, so you crippled your system with this hack.