Hello !
I've a fresh install of proxmox 6.
I've create a CT debian 10, with external FO ip
I want to use the firewall to limit access to the CT, and filtering on source ips.
but If I set source IP in the container, the traffic was not allowed. I need to set the source as the ip of the promox host !
A rule without source is OK.
A rule with source different than the host is bocking.
As is proxmox was a router and the only visible source ip was the proxmox.
But I want to use my external ip directly.
Maybe a config of the bridge interface ?
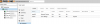


I've a fresh install of proxmox 6.
I've create a CT debian 10, with external FO ip
I want to use the firewall to limit access to the CT, and filtering on source ips.
but If I set source IP in the container, the traffic was not allowed. I need to set the source as the ip of the promox host !
A rule without source is OK.
A rule with source different than the host is bocking.
As is proxmox was a router and the only visible source ip was the proxmox.
But I want to use my external ip directly.
Maybe a config of the bridge interface ?
Attachments
Last edited:

