Hi!
SDNs is a great step forward on Proxmox VE.
I'm trying to use SND and Firewall to create a DMZ. The idea is to improve the security of my homelab and my internal network (LAN), once I have some services publicly exposed.
I'm using Cloudflare Tunnel (great service, by the way), but I don't feel comfortable putting the tunnel endpoint (cloudflared deamon) inside my LAN. I prefer to install the tunnel endpoint into a DMZ with no access to my LAN.
To improve the performance, when my users are connected to the LAN, the ideal is that my LAN have direct access to my DMZ.
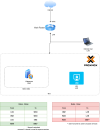
I already have success creating this environment in two different scenarios:
1 – using only a main router and VLAN SDN.
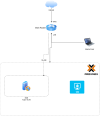
2 - using a main router and an internal router to connect an isolated VLAN SDN for DMZ.
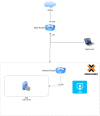
I also tried to create a Simple SDN and use the same strategy that I had successfully used with an internal router, but I'm facing a problem: My Proxmox configuration is a 3 hosts cluster. In this scenario there are no router static IP to route traffic from LAN to DMZ. I already tried to use keepalived to provide a VIP to my cluster, but if host A receives a package for some VM in host B, this package is dropped. Even when I tried to use an internal router, the Simple SDN isn't a solution. The problem, as I tested, is that Simple SDN is isolated by host. It means that a VM on host A can't communicate with a VM on host B, even when both are in the same Simple SDN. That makes it hard to find a real-life use case to implement a Simple SDNs as a solution when you have a Proxmox cluster.
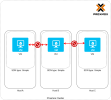
Am I doing something wrong with setting up simple SDNs?
SDNs is a great step forward on Proxmox VE.
I'm trying to use SND and Firewall to create a DMZ. The idea is to improve the security of my homelab and my internal network (LAN), once I have some services publicly exposed.
I'm using Cloudflare Tunnel (great service, by the way), but I don't feel comfortable putting the tunnel endpoint (cloudflared deamon) inside my LAN. I prefer to install the tunnel endpoint into a DMZ with no access to my LAN.
To improve the performance, when my users are connected to the LAN, the ideal is that my LAN have direct access to my DMZ.

I already have success creating this environment in two different scenarios:
1 – using only a main router and VLAN SDN.
- Pros: no additional software installation will be required; the process will be simplified.
- Cons: The operation will be fully dependent of your main router (single point of failure)

2 - using a main router and an internal router to connect an isolated VLAN SDN for DMZ.
- Pros: Decentralized management (main router North-South, internal router East-West).
- Cons: More work must be done to make things operational; one more VM to give maintenance.

I also tried to create a Simple SDN and use the same strategy that I had successfully used with an internal router, but I'm facing a problem: My Proxmox configuration is a 3 hosts cluster. In this scenario there are no router static IP to route traffic from LAN to DMZ. I already tried to use keepalived to provide a VIP to my cluster, but if host A receives a package for some VM in host B, this package is dropped. Even when I tried to use an internal router, the Simple SDN isn't a solution. The problem, as I tested, is that Simple SDN is isolated by host. It means that a VM on host A can't communicate with a VM on host B, even when both are in the same Simple SDN. That makes it hard to find a real-life use case to implement a Simple SDNs as a solution when you have a Proxmox cluster.

Am I doing something wrong with setting up simple SDNs?
Last edited:

