Hello all,
I currently have a single nic on my proxmox host and am using two bridges as wan and lan for my pfsense vm where all traffic goes through.
Now I wanted to passthrough the nic into the vm in order to allow for better performance.
I followed the info at https://pve.proxmox.com/wiki/PCI_Passthrough
However, when I add the nic to pci-passthrough for my vm, I lose all connections. The kvm gets no info, also soft shutdown (hetzner calls it "pressing the power button" does not work anymore and I have to do a hard shutdown.
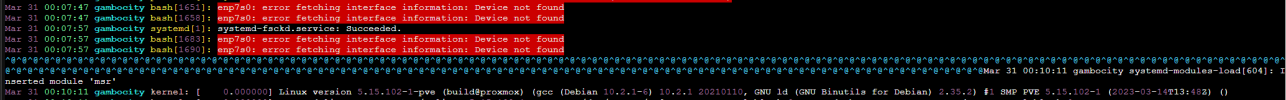
I have attached some log messages which might provide more insight. On my pfsense
The "device not found" error from bash is not out of the ordinary since a script was trying to access the passthroughed nic's interface.
I currently have a single nic on my proxmox host and am using two bridges as wan and lan for my pfsense vm where all traffic goes through.
Now I wanted to passthrough the nic into the vm in order to allow for better performance.
I followed the info at https://pve.proxmox.com/wiki/PCI_Passthrough
However, when I add the nic to pci-passthrough for my vm, I lose all connections. The kvm gets no info, also soft shutdown (hetzner calls it "pressing the power button" does not work anymore and I have to do a hard shutdown.
I have attached some log messages which might provide more insight. On my pfsense
/var/log/system I could not find any entries at the corresponding times.The "device not found" error from bash is not out of the ordinary since a script was trying to access the passthroughed nic's interface.