Hello all.
Doesn't take much, but here's what I have.
pve -
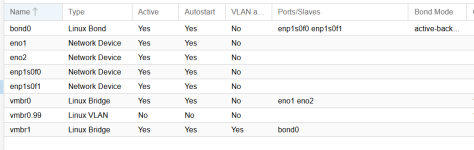
From what I am trying to understand -
eno1 and eno2 are active and in the bridge of vmbro.
Both interfaces are active and 1 is being used for mgmt, and the other is where my vlan's are running out of.
The box0 is running off of 2 different interfaces, enp1s0f0 and enp1sof1 - and configured in a active/backup solution.
pvepbr - 2nd box in cluster
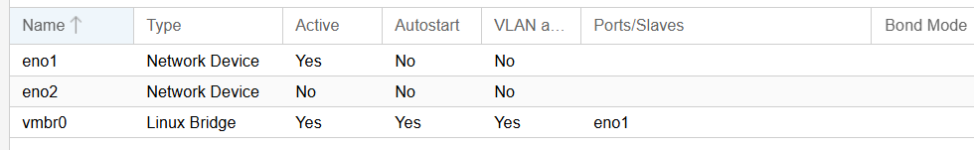
Only 1 interface is active - due to issues on the switch, which i can't get into.
Whenever I 'migrate' from 1 server to another, and there is a vlan associated with it from PVE server, i have to stop/migrate/adjust the vlan from what it should be, to the 'default' vlan on pvepbr.
What I'm trying to do is essentially the same on pvepbr as on pve - create a bridge which can accept the different vlans on it (specified on the hardware/vlan setting as well as (somehow) create a bond whereby the managment port is dedicated to 1 of the interfaces on pvepbr, and the 2nd interface is handling all the different vlans.
Since this is in production currently, how can i do this?
I can, if need be - migrate all servers from the 2nd box, pvepbr, over to pve and make changes as needed.
I was unsure if i needed to create the bond first, and associated it with the 2 interfaces (eno1 and eno2) but as eno2 wasn't connected to the switch - I was unsure.
If I do this, then connect the 2nd interface to the switch - what will happen to connectivity to the box? Will the 'bond' now start advertising as the new ip, currently associated with the server?
After this is done, then presumably I can create the bridge and add the bond0 to it. ???
How does the system know which address or interface that the vlans are running on, vs the mgmt port?
thanks in advance, and can provide more info if needed.
Doesn't take much, but here's what I have.
pve -

From what I am trying to understand -
eno1 and eno2 are active and in the bridge of vmbro.
Both interfaces are active and 1 is being used for mgmt, and the other is where my vlan's are running out of.
The box0 is running off of 2 different interfaces, enp1s0f0 and enp1sof1 - and configured in a active/backup solution.
pvepbr - 2nd box in cluster

Only 1 interface is active - due to issues on the switch, which i can't get into.
Whenever I 'migrate' from 1 server to another, and there is a vlan associated with it from PVE server, i have to stop/migrate/adjust the vlan from what it should be, to the 'default' vlan on pvepbr.
What I'm trying to do is essentially the same on pvepbr as on pve - create a bridge which can accept the different vlans on it (specified on the hardware/vlan setting as well as (somehow) create a bond whereby the managment port is dedicated to 1 of the interfaces on pvepbr, and the 2nd interface is handling all the different vlans.
Since this is in production currently, how can i do this?
I can, if need be - migrate all servers from the 2nd box, pvepbr, over to pve and make changes as needed.
I was unsure if i needed to create the bond first, and associated it with the 2 interfaces (eno1 and eno2) but as eno2 wasn't connected to the switch - I was unsure.
If I do this, then connect the 2nd interface to the switch - what will happen to connectivity to the box? Will the 'bond' now start advertising as the new ip, currently associated with the server?
After this is done, then presumably I can create the bridge and add the bond0 to it. ???
How does the system know which address or interface that the vlans are running on, vs the mgmt port?
thanks in advance, and can provide more info if needed.

