Hi,
I'm currently splitting up my network in multiple subnets and VLANs but stumbled on something with Proxmox, I don't quite understand:
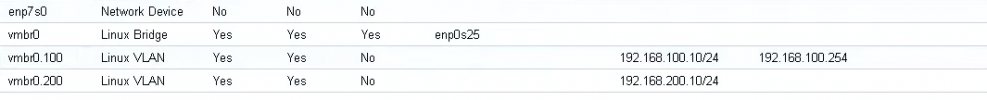
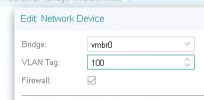
What do we create these subinterfaces (vmbr0.100, vmbr0.200) for, as in the final configuration of VMs/CTs we won't select any of those, but rather the parent interface and specify the VID manually.
And secondly, in general, when there are multiple interfaces configured, which one does PVE use for its own communication?
Maybe I'm overthinking things ... but currently I'm kind of stuck with these thoughts ^^
Any clarification is well appreciated!
I'm currently splitting up my network in multiple subnets and VLANs but stumbled on something with Proxmox, I don't quite understand:

What do we create these subinterfaces (vmbr0.100, vmbr0.200) for, as in the final configuration of VMs/CTs we won't select any of those, but rather the parent interface and specify the VID manually.
And secondly, in general, when there are multiple interfaces configured, which one does PVE use for its own communication?
Maybe I'm overthinking things ... but currently I'm kind of stuck with these thoughts ^^
Any clarification is well appreciated!
Last edited: