Did a clean/fresh install of teh PVE 5.2 iso.
Started restoring the kvms and containers.
VMs restored fine.
Container "appeared" to restore fine.
However when I go to start the container:
command 'systemctl start pve-container@100' failed: exit code 1
Logs and versions below.
So I tried to create a fresh container, but no templates are listed during the creation process:

But I do seem them in local:
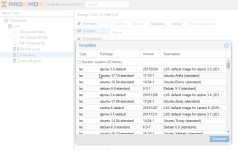
I am not sure if these are related or not.
Following some other threads, I made sure the pve no sub repo was in the source list, I disabled the subscription one, and ran apt-get update and then apt-get full-upgrade.
Still no luck.
Any thoughts would be greatly appreciated!
Looking at the service status:
Jun 16 11:48:40 pve systemd[1]: Starting PVE LXC Container: 100...
Jun 16 11:48:40 pve lxc-start[3918]: lxc-start: 100: lxccontainer.c: wait_on_daemonized_start: 815 No such file or directory - Failed to receive the container state
Jun 16 11:48:40 pve lxc-start[3918]: The container failed to start.
Jun 16 11:48:40 pve lxc-start[3918]: To get more details, run the container in foreground mode.
Jun 16 11:48:40 pve lxc-start[3918]: Additional information can be obtained by setting the --logfile and --logpriority options.
Jun 16 11:48:40 pve systemd[1]: pve-container@100.service: Control process exited, code=exited status=1
Jun 16 11:48:40 pve systemd[1]: Failed to start PVE LXC Container: 100.
Jun 16 11:48:40 pve systemd[1]: pve-container@100.service: Unit entered failed state.
Jun 16 11:48:40 pve systemd[1]: pve-container@100.service: Failed with result 'exit-code'.
root@pve:/etc/apt/sources.list.d# apt-get upgrade
Reading package lists... Done
Building dependency tree
Reading state information... Done
Calculating upgrade... Done
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
root@pve:/etc/apt/sources.list.d# pveversion -v
proxmox-ve: 5.2-2 (running kernel: 4.15.17-3-pve)
pve-manager: 5.2-2 (running version: 5.2-2/b1d1c7f4)
pve-kernel-4.15: 5.2-3
pve-kernel-4.15.17-3-pve: 4.15.17-12
pve-kernel-4.15.17-1-pve: 4.15.17-9
corosync: 2.4.2-pve5
criu: 2.11.1-1~bpo90
glusterfs-client: 3.8.8-1
ksm-control-daemon: 1.2-2
libjs-extjs: 6.0.1-2
libpve-access-control: 5.0-8
libpve-apiclient-perl: 2.0-4
libpve-common-perl: 5.0-32
libpve-guest-common-perl: 2.0-16
libpve-http-server-perl: 2.0-9
libpve-storage-perl: 5.0-23
libqb0: 1.0.1-1
lvm2: 2.02.168-pve6
lxc-pve: 3.0.0-3
lxcfs: 3.0.0-1
novnc-pve: 1.0.0-1
proxmox-widget-toolkit: 1.0-18
pve-cluster: 5.0-27
pve-container: 2.0-23
pve-docs: 5.2-4
pve-firewall: 3.0-11
pve-firmware: 2.0-4
pve-ha-manager: 2.0-5
pve-i18n: 1.0-6
pve-libspice-server1: 0.12.8-3
pve-qemu-kvm: 2.11.1-5
pve-xtermjs: 1.0-5
qemu-server: 5.0-28
smartmontools: 6.5+svn4324-1
spiceterm: 3.0-5
vncterm: 1.5-3
zfsutils-linux: 0.7.9-pve1~bpo9
root@pve:/etc/apt/sources.list.d# cd /
root@pve:/# /usr/bin/lxc-start -n 100 -F -lDEBUG -o /dev/shm/err.log --logpriority TRACE
lxc-start: 100: conf.c: run_buffer: 347 Script exited with status 2
lxc-start: 100: start.c: lxc_init: 815 Failed to run lxc.hook.pre-start for container "100"
lxc-start: 100: start.c: __lxc_start: 1849 Failed to initialize container "100"
The container failed to start.
Additional information can be obtained by setting the --logfile and --logpriority options.
root@pve:/# cat /dev/shm/err.log
lxc-start 100 20180616155248.243 TRACE lxc_commands - commands.c:lxc_cmd:311 - Connection refused - Command "get_init_pid" failed to connect command socket
lxc-start 100 20180616155248.243 TRACE lxc_commands - commands.c:lxc_cmd:311 - Connection refused - Command "get_cgroup" failed to connect command socket
lxc-start 100 20180616155248.243 TRACE lxc_commands - commands.c:lxc_cmd:311 - Connection refused - Command "get_state" failed to connect command socket
lxc-start 100 20180616155248.243 TRACE lxc_commands - commands.c:lxc_cmd_init:1291 - Creating abstract unix socket "/var/lib/lxc/100/command"
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init_handler:714 - Unix domain socket 4 for command server is ready
lxc-start 100 20180616155248.243 INFO lxc_lsm - lsm/lsm.c:lsm_init:46 - LSM security driver AppArmor
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init:731 - Initialized LSM
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:585 - processing: .reject_force_umount # comment this to allow umount -f; not recommended
arse_config_v2:585 - processing: .reject_force_umount # comment this to allow umount -f; not recommended
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:761 - Adding native rule for reject_force_umount # comment this to allow umount -f; not recommended action 0(kill)
arse_config_v2:761 - Adding native rule for reject_force_umount # comment this to allow umount -f; not recommended action 0(kill)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:411 - Setting Seccomp rule to reject force umounts
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:765 - Adding compat rule for reject_force_umount action 0(kill)
arse_config_v2:765 - Adding compat rule for reject_force_umount action 0(kill)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:411 - Setting Seccomp rule to reject force umounts
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:411 - Setting Seccomp rule to reject force umounts
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:585 - processing: .[all]
arse_config_v2:585 - processing: .[all]
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:585 - processing: .kexec_load errno 1
arse_config_v2:585 - processing: .kexec_load errno 1
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:761 - Adding native rule for kexec_load errno 1 action 327681(errno)
arse_config_v2:761 - Adding native rule for kexec_load errno 1 action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:765 - Adding compat rule for kexec_load action 327681(errno)
arse_config_v2:765 - Adding compat rule for kexec_load action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:585 - processing: .open_by_handle_at errno 1
arse_config_v2:585 - processing: .open_by_handle_at errno 1
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:761 - Adding native rule for open_by_handle_at errno 1 action 327681(errno)
arse_config_v2:761 - Adding native rule for open_by_handle_at errno 1 action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:765 - Adding compat rule for open_by_handle_at action 327681(errno)
arse_config_v2:765 - Adding compat rule for open_by_handle_at action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:585 - processing: .init_module errno 1
arse_config_v2:585 - processing: .init_module errno 1
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:761 - Adding native rule for init_module errno 1 action 327681(errno)
arse_config_v2:761 - Adding native rule for init_module errno 1 action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:765 - Adding compat rule for init_module action 327681(errno)
arse_config_v2:765 - Adding compat rule for init_module action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:585 - processing: .finit_module errno 1
arse_config_v2:585 - processing: .finit_module errno 1
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:761 - Adding native rule for finit_module errno 1 action 327681(errno)
arse_config_v2:761 - Adding native rule for finit_module errno 1 action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:765 - Adding compat rule for finit_module action 327681(errno)
arse_config_v2:765 - Adding compat rule for finit_module action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:585 - processing: .delete_module errno 1
arse_config_v2:585 - processing: .delete_module errno 1
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:761 - Adding native rule for delete_module errno 1 action 327681(errno)
arse_config_v2:761 - Adding native rule for delete_module errno 1 action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:765 - Adding compat rule for delete_module action 327681(errno)
arse_config_v2:765 - Adding compat rule for delete_module action 327681(errno)
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c arse_config_v2:775 - Merging in the compat Seccomp ctx into the main one
arse_config_v2:775 - Merging in the compat Seccomp ctx into the main one
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init:738 - Read seccomp policy
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_serve_state_clients:423 - Set container state to STARTING
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_serve_state_clients:426 - No state clients registered
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init:746 - Set container state to "STARTING"
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init:811 - Set environment variables
lxc-start 100 20180616155248.243 INFO lxc_conf - conf.c:run_script_argv:368 - Executing script "/usr/share/lxc/hooks/lxc-pve-prestart-hook" for container "100", config section "lxc"
lxc-start 100 20180616155248.528 DEBUG lxc_conf - conf.c:run_buffer:338 - Script exec /usr/share/lxc/hooks/lxc-pve-prestart-hook 100 lxc pre-start with output: directory '/lxcshare' does not exist
lxc-start 100 20180616155248.533 ERROR lxc_conf - conf.c:run_buffer:347 - Script exited with status 2
lxc-start 100 20180616155248.533 ERROR lxc_start - start.c:lxc_init:815 - Failed to run lxc.hook.pre-start for container "100"
lxc-start 100 20180616155248.533 TRACE lxc_start - start.c:lxc_serve_state_clients:423 - Set container state to ABORTING
lxc-start 100 20180616155248.533 TRACE lxc_start - start.c:lxc_serve_state_clients:426 - No state clients registered
lxc-start 100 20180616155248.533 ERROR lxc_start - start.c:__lxc_start:1849 - Failed to initialize container "100"
Started restoring the kvms and containers.
VMs restored fine.
Container "appeared" to restore fine.
However when I go to start the container:
command 'systemctl start pve-container@100' failed: exit code 1
Logs and versions below.
So I tried to create a fresh container, but no templates are listed during the creation process:

But I do seem them in local:

I am not sure if these are related or not.
Following some other threads, I made sure the pve no sub repo was in the source list, I disabled the subscription one, and ran apt-get update and then apt-get full-upgrade.
Still no luck.
Any thoughts would be greatly appreciated!
Looking at the service status:
Jun 16 11:48:40 pve systemd[1]: Starting PVE LXC Container: 100...
Jun 16 11:48:40 pve lxc-start[3918]: lxc-start: 100: lxccontainer.c: wait_on_daemonized_start: 815 No such file or directory - Failed to receive the container state
Jun 16 11:48:40 pve lxc-start[3918]: The container failed to start.
Jun 16 11:48:40 pve lxc-start[3918]: To get more details, run the container in foreground mode.
Jun 16 11:48:40 pve lxc-start[3918]: Additional information can be obtained by setting the --logfile and --logpriority options.
Jun 16 11:48:40 pve systemd[1]: pve-container@100.service: Control process exited, code=exited status=1
Jun 16 11:48:40 pve systemd[1]: Failed to start PVE LXC Container: 100.
Jun 16 11:48:40 pve systemd[1]: pve-container@100.service: Unit entered failed state.
Jun 16 11:48:40 pve systemd[1]: pve-container@100.service: Failed with result 'exit-code'.
root@pve:/etc/apt/sources.list.d# apt-get upgrade
Reading package lists... Done
Building dependency tree
Reading state information... Done
Calculating upgrade... Done
0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded.
root@pve:/etc/apt/sources.list.d# pveversion -v
proxmox-ve: 5.2-2 (running kernel: 4.15.17-3-pve)
pve-manager: 5.2-2 (running version: 5.2-2/b1d1c7f4)
pve-kernel-4.15: 5.2-3
pve-kernel-4.15.17-3-pve: 4.15.17-12
pve-kernel-4.15.17-1-pve: 4.15.17-9
corosync: 2.4.2-pve5
criu: 2.11.1-1~bpo90
glusterfs-client: 3.8.8-1
ksm-control-daemon: 1.2-2
libjs-extjs: 6.0.1-2
libpve-access-control: 5.0-8
libpve-apiclient-perl: 2.0-4
libpve-common-perl: 5.0-32
libpve-guest-common-perl: 2.0-16
libpve-http-server-perl: 2.0-9
libpve-storage-perl: 5.0-23
libqb0: 1.0.1-1
lvm2: 2.02.168-pve6
lxc-pve: 3.0.0-3
lxcfs: 3.0.0-1
novnc-pve: 1.0.0-1
proxmox-widget-toolkit: 1.0-18
pve-cluster: 5.0-27
pve-container: 2.0-23
pve-docs: 5.2-4
pve-firewall: 3.0-11
pve-firmware: 2.0-4
pve-ha-manager: 2.0-5
pve-i18n: 1.0-6
pve-libspice-server1: 0.12.8-3
pve-qemu-kvm: 2.11.1-5
pve-xtermjs: 1.0-5
qemu-server: 5.0-28
smartmontools: 6.5+svn4324-1
spiceterm: 3.0-5
vncterm: 1.5-3
zfsutils-linux: 0.7.9-pve1~bpo9
root@pve:/etc/apt/sources.list.d# cd /
root@pve:/# /usr/bin/lxc-start -n 100 -F -lDEBUG -o /dev/shm/err.log --logpriority TRACE
lxc-start: 100: conf.c: run_buffer: 347 Script exited with status 2
lxc-start: 100: start.c: lxc_init: 815 Failed to run lxc.hook.pre-start for container "100"
lxc-start: 100: start.c: __lxc_start: 1849 Failed to initialize container "100"
The container failed to start.
Additional information can be obtained by setting the --logfile and --logpriority options.
root@pve:/# cat /dev/shm/err.log
lxc-start 100 20180616155248.243 TRACE lxc_commands - commands.c:lxc_cmd:311 - Connection refused - Command "get_init_pid" failed to connect command socket
lxc-start 100 20180616155248.243 TRACE lxc_commands - commands.c:lxc_cmd:311 - Connection refused - Command "get_cgroup" failed to connect command socket
lxc-start 100 20180616155248.243 TRACE lxc_commands - commands.c:lxc_cmd:311 - Connection refused - Command "get_state" failed to connect command socket
lxc-start 100 20180616155248.243 TRACE lxc_commands - commands.c:lxc_cmd_init:1291 - Creating abstract unix socket "/var/lib/lxc/100/command"
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init_handler:714 - Unix domain socket 4 for command server is ready
lxc-start 100 20180616155248.243 INFO lxc_lsm - lsm/lsm.c:lsm_init:46 - LSM security driver AppArmor
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init:731 - Initialized LSM
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:411 - Setting Seccomp rule to reject force umounts
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:411 - Setting Seccomp rule to reject force umounts
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c:do_resolve_add_rule:411 - Setting Seccomp rule to reject force umounts
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 INFO lxc_seccomp - seccomp.c
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init:738 - Read seccomp policy
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_serve_state_clients:423 - Set container state to STARTING
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_serve_state_clients:426 - No state clients registered
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init:746 - Set container state to "STARTING"
lxc-start 100 20180616155248.243 TRACE lxc_start - start.c:lxc_init:811 - Set environment variables
lxc-start 100 20180616155248.243 INFO lxc_conf - conf.c:run_script_argv:368 - Executing script "/usr/share/lxc/hooks/lxc-pve-prestart-hook" for container "100", config section "lxc"
lxc-start 100 20180616155248.528 DEBUG lxc_conf - conf.c:run_buffer:338 - Script exec /usr/share/lxc/hooks/lxc-pve-prestart-hook 100 lxc pre-start with output: directory '/lxcshare' does not exist
lxc-start 100 20180616155248.533 ERROR lxc_conf - conf.c:run_buffer:347 - Script exited with status 2
lxc-start 100 20180616155248.533 ERROR lxc_start - start.c:lxc_init:815 - Failed to run lxc.hook.pre-start for container "100"
lxc-start 100 20180616155248.533 TRACE lxc_start - start.c:lxc_serve_state_clients:423 - Set container state to ABORTING
lxc-start 100 20180616155248.533 TRACE lxc_start - start.c:lxc_serve_state_clients:426 - No state clients registered
lxc-start 100 20180616155248.533 ERROR lxc_start - start.c:__lxc_start:1849 - Failed to initialize container "100"

