Close reject options
- Thread starter digiweb
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I don't understand the question - please try to explain it some more and provide some logs ?
the DNSBL Sites setting are the dnsbl lists used by postscreen:
http://www.postfix.org/POSTSCREEN_README.html
Usually you really want to:
* select some good dnsbls, which are reliable
* don't process the mails coming from IPs which are listed there
everything else wastes resources
in other words - if spamcop lists ips from which you want to receive mail - do not add it to DNSBL sites
see https://pmg.proxmox.com/wiki/index.php/Getting_started_with_Proxmox_Mail_Gateway
for a setup that does work quite well in practice
the DNSBL Sites setting are the dnsbl lists used by postscreen:
http://www.postfix.org/POSTSCREEN_README.html
Usually you really want to:
* select some good dnsbls, which are reliable
* don't process the mails coming from IPs which are listed there
everything else wastes resources
in other words - if spamcop lists ips from which you want to receive mail - do not add it to DNSBL sites
see https://pmg.proxmox.com/wiki/index.php/Getting_started_with_Proxmox_Mail_Gateway
for a setup that does work quite well in practice
As said it's nothing I would recommend ... but anyways:the system does not reject any mail. Quarantine the emails that need to be rejected.
* do not set any DNSBL's in mailproxy->options
then all your mails will be checked against spamassassin's default list of dnsbls:
https://cwiki.apache.org/confluence/display/spamassassin/DnsBlocklists
you can increase the score of certain lists if they work better for you to make sure the mails have enought points to end up in quarantine with your ruleset
@Stoiko Ivanov by executing the RBL at the SpamAssasin level, this will allow the ability to whitelist, as well as add statistics showing more messages blocked within PMG?
Thanks
Thanks
not sure I understand your question 100%.., but@Stoiko Ivanov by executing the RBL at the SpamAssasin level, this will allow the ability to whitelist, as well as add statistics showing more messages blocked within PMG?
* not using dnsbl_sites (i.e. postscreen's dnsbl) means you do not need to whitelist IPs in the mailproxy whitelist (and can rather use the rulesystem)
* the statistics will not show the mails als junk and rejected ..
I hope this helps!
For us `zen.spamhaus.org` and `b.barracudacentral.org ` yield quite good results without any false-postives...When using dnsbl, often good emails end up in spam lists.
And with the advantage of not wasting resources for scanning the mail - I would really recommend to configure (a few good) dnsbls for blocking before the smtp-dialog in almost all use-cases
as explained in a few threads in this forum - if you don't want that - just don't enter any dnsbl_sites and spamassassin will analyze the mails and assign points.
This is not possible - the dnsbl_sites setting in the Mail Proxy has nothing to do with the rule-system - it uses postscreen to quickly reject listed IPs see:I want to use the dnsbl feature.
but if an incoming mail is found in one of the dnsbl lists, I want it to "quarantine" instead of "reject".
https://www.postfix.org/POSTSCREEN_README.html
some DNS bl checks are implemented in SpamAssassin - you can raise their score with a custom score and then quarantine mails with a high score - but keep in mind that your system will have to process quite a lot more of junk that would otherwise have been rejected right out of the box...
@digiweb
If I'm not misunderstanding, I believe you are wanting to take a blacklist, and rather than bounce it as it comes in, quarantine it.
I know I do this with RBL's via SpamAssasin, and I believe you can also do it with dnsbl's as well.
In my below example is how I use RBL's within SA to quarantine.
I'm sure google will have proper examples for DNSBL's.
One side note, whenever I uncomment these additional SA settings, the amount of quarantine messages jumps 5 to 10 times the amount of messages normally seen in quarantine.
If I'm not misunderstanding, I believe you are wanting to take a blacklist, and rather than bounce it as it comes in, quarantine it.
I know I do this with RBL's via SpamAssasin, and I believe you can also do it with dnsbl's as well.
In my below example is how I use RBL's within SA to quarantine.
I'm sure google will have proper examples for DNSBL's.
One side note, whenever I uncomment these additional SA settings, the amount of quarantine messages jumps 5 to 10 times the amount of messages normally seen in quarantine.
#RBL's
#header RCVD_IN_ZENSPAMHAUS eval:check_rbl('zenspamhaus-lastexternal', 'zen.spamhaus.org.')
#describe RCVD_IN_ZENSPAMHAUS Relay is listed in zen.spamhaus.org
#tflags RCVD_IN_ZENSPAMHAUS net
#score RCVD_IN_ZENSPAMHAUS 5.0
#header RCVD_IN_BARRACUDACEN eval:check_rbl('bbarracuda-lastexternal', 'b.barracudacentral.org.')
#describe RCVD_IN_BARRACUDACEN Relay is listed in b.barracudacentral.org
#tflags RCVD_IN_BARRACUDACEN net
#score RCVD_IN_BARRACUDACEN 5.0
Actually, the problem I want to solve is this;
abc@.com is my customer using antispam.
xyz.com is a supplier company that sends mail to him from outside
- The ip addresses of xyz.com mail servers are blacklisted.
- therefore the mail is being rejected.
- Since xyz.com is a person we know, I want this email to be forwarded to us or quarantined.
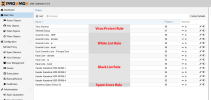
- Let's set up a "trusted list" before the "spam score" rule. But still this mail is rejected.
abc@.com is my customer using antispam.
xyz.com is a supplier company that sends mail to him from outside
- The ip addresses of xyz.com mail servers are blacklisted.
- therefore the mail is being rejected.
- Since xyz.com is a person we know, I want this email to be forwarded to us or quarantined.
- Let's set up a "trusted list" before the "spam score" rule. But still this mail is rejected.
Attachments
@digiweb I think the safer method especially if the sender uses public servers is to do the blacklist in SA.
I did mention some of my experience within my previous response, now you say you really want to just allow it, I would say Proceed with caution!
There could be many spammers on the "same IP" so all that spam would be accepted, no exceptions.
In the past I have used this method:
If you're not familiar with postfix or some of the more advanced configurations, I would say get help.
On the server directly via shell, I create a file called clientaccess/cidr_allow (you can name it whatever you want).
One IP per line for each IP you want to whitelist.
the clientaccess file:
1.2.3.4 OK
2.3.4.5 OK
main.cf needs
smtpd_sender_restrictions =
check_client_access cidr:/etc/postfix/clientaccess
because you need the entry in main.cf, but PMG generates the file, you will need to modify the postfix template from PMG.
Again, be certain what you are doing, and then after you update that, I believe you have to restart PMG and it should generate the new main.cf and you can confirm the new value has been added.
Restart postfix and test.
I'm pretty sure I have these written these general steps correctly, but double checking is always advised.
I did mention some of my experience within my previous response, now you say you really want to just allow it, I would say Proceed with caution!
There could be many spammers on the "same IP" so all that spam would be accepted, no exceptions.
In the past I have used this method:
If you're not familiar with postfix or some of the more advanced configurations, I would say get help.
On the server directly via shell, I create a file called clientaccess/cidr_allow (you can name it whatever you want).
One IP per line for each IP you want to whitelist.
the clientaccess file:
1.2.3.4 OK
2.3.4.5 OK
main.cf needs
smtpd_sender_restrictions =
check_client_access cidr:/etc/postfix/clientaccess
because you need the entry in main.cf, but PMG generates the file, you will need to modify the postfix template from PMG.
Again, be certain what you are doing, and then after you update that, I believe you have to restart PMG and it should generate the new main.cf and you can confirm the new value has been added.
Restart postfix and test.
I'm pretty sure I have these written these general steps correctly, but double checking is always advised.